Endpoint Event Schema 1.1.0
The Carbon Black Cloud Endpoint Event Schema has been updated to version 1.1.0!
New in 1.1.0
- XDR Data - VMware Carbon Black Extended Detection and Response (XDR) greatly enhances security detections by reporting on network telemetry at the sensor level to detect lateral security movement across your fleet.
- Security teams can leverage VMware Carbon Black XDR to quickly identify threats across their environment and make better-informed decisions in applying prevention policies.
- New fields can be easily found in the table below by filtering for
1.1.0in the name column. It uses hidden text on the icon.
- Schema Versioning - The schema version will be included in the API response, and users can configure which schema version they would like to use in the Carbon Black Cloud console.
- See the Announcement Blog for details, including how to update an existing Forwarder
Customers who want to receive XDR-enhanced endpoint events data must subscribe to the XDR add-on for Enterprise EDR and then opt-in to schema version 1.1.0 by configuring your Data Forwarder in the Carbon Black Cloud console.
Legend
New fields
New fields since the previous schema version are denoted with a yellow bar
v1.1.0
at the left of the table row. You can easily isolate these by typing 1.1.0 in the Field Name filter box.
Capabilities
- NOT FILTERABLE - Indicates when the field is not supported in the query for a filter. Most fields can be used in filters.
- TOKENIZED - The field supports partial phrase matching through Tokenization
- ENDPOINT STANDARD - Fields specific to the Endpoint Standard product
- ENTERPRISE EDR - Fields specific to the Enterprise EDR product
- XDR - Additional fields populated when the XDR feature add on is enabled
Wildcards - All fields support wildcard characters. Tips on filtering and recommended practices are in the Carbon Black Cloud User Guide.
Event Type
The following list contains the event types used in Carbon Black Cloud. You can search by each of these event types in the Fields table below.
COMMON- The Carbon Black Cloud Data Forwarder emits a set of common fields for every endpoint event. These fields represent common metadata for the organization, device, and process to which this event belongs. Some fields are only populated by specific products; this is identified by Capability.
CROSSPROC- Any time a process interacts with another process on the system, that is considered a “cross-process” event. Each cross-process event is reported as the type “endpoint.event.crossproc”.
FILEMOD- Each file-modification event is reported as the type “endpoint.event.filemod”.
FILELESS SCRIPTLOAD- A “fileless script load” is generated when a process loads a set of script instructions into memory. Each fileless script load event is reported as the type “endpoint.event.fileless_scriptload”.
MODULE LOAD- A “module load” is generated when a process loads a shared library (DLL in Windows, .so in Linux, .dylib in macOS) into its process memory space. Each module load event is reported as the type “endpoint.event.moduleload”.
NETCONN- Each network-connection event is reported as the type “endpoint.event.netconn”. See example below.
NETCONN PROXY- A “network proxy connection” event is any network connection event in which the process communicates with an intermediary remote device but has a different intended destination - usually an HTTP proxy intermediary. Each network proxy connection event is reported as the type “endpoint.event.netconn_proxy”.
PROCSTART- Each process launch event is reported as the type “endpoint.event.procstart”. A procstart event can be either a child process or a new process. A child process event will have the actionACTION_CREATE_PROCESSwhere a new process will haveACTION_PROCESS_DISCOVERED. In the case of a new process you will only haveprocessandchildprocproperties, there will be noparentproperties. The child process properties represent the process being created and the process properties will represent the os system. Thetarget_cmdlineproperty is the command line that was executed to create the process represented in thechildprocproperties. See example below.
REGMOD- Each registry-modification event is reported as the type “endpoint.event.regmod”.
SCRIPTLOAD- A “script load” is generated when a process loads a script (.ps1, .vb, .bin, etc.) that can be executed by a script interpreter. Each script load event is reported as the type “endpoint.event.scriptload”.
Fields
Note: Certain fields that were previously included in this listing, but were never actually populated, have been removed.| Field Name | Definition | Datatype | Capabilities
All fields support wildcards |
Event Type |
|---|---|---|---|---|
action |
Specific endpoint action observed by sensor during this event. Enum values vary by event type |
String | COMMON |
|
alert_id |
The ID of the Alert this event is associated with | String | ENDPOINT STANDARD | COMMON |
backend_timestamp |
Time when the backend received the batch of events, based on Carbon Black Cloud backend’s clock as an RFC 3339 formatted time string based on UTC to the seconds; may differ from device_timestamp by a few minutes due to asynchronous processing
Example: 2021-07-28 18:43:51 +0000 UTC |
ISO 8601 UTC timestamp | NOT FILTERABLE | COMMON |
childproc_guid |
Unique ID of the child process. See this document for more information on how a process GUID is used and each of its components. | String | NOT FILTERABLE | PROCSTART |
childproc_hash |
Cryptographic hashes of the executable file backing the child process, represented as an array of two elements - MD5 and SHA-256 hash | String[] | PROCSTART |
|
childproc_name |
Full path to the target application for the child process on the device’s local file system | String | PROCSTART |
|
childproc_pid |
OS-reported Process ID of the child process | String | PROCSTART |
|
childproc_publisher[]
.name |
Array with objects of two keys: “name” and “state”. Each array entry is a signature entry for the childproc as reported by the endpoint | String | Filterable field: childproc_publisher |
PROCSTART |
childproc_publisher[]
.state |
See above | String | Filterable field: childproc_publisher_state |
PROCSTART |
childproc_reputation |
Carbon Black Cloud Reputation string for the childproc. | String | PROCSTART |
|
childproc_username |
The username associated with the user context that the child process was started under | String | PROCSTART |
|
crossproc_api |
Name of the operating system API called by the actor process. In cases where that call targets another process, that process is reported as crossproc_name. In cases where there is no target process, this field represents a system API call.
Available with:
|
String | CROSSPROC |
|
crossproc_action |
The cross-process action initiated by the actor process
ACTION_API_CALL, ACTION_DUP_PROCESS_HANDLE, ACTION_OPEN_THREAD_HANDLE, ACTION_DUP_THREAD_HANDLE, ACTION_CREATE_REMOTE_THREAD |
String | CROSSPROC |
|
crossproc_guid |
Unique ID of the cross process | String | NOT FILTERABLE | CROSSPROC |
crossproc_hash |
Cryptographic hashes of the target of the crossproc event — this is represented as an array of two elements, MD5 and SHA-256 hash | String[] | CROSSPROC |
|
crossproc_name |
Full path to the target of the crossproc event on the device’s local file system | String | CROSSPROC |
|
crossproc_publisher[]
.name |
Array with objects of two keys: “name” and “state”. Each array entry is a signature entry for the crossproc as reported by the endpoint | Object | Filterable field: crossproc_publisher |
CROSSPROC |
crossproc_publisher[]
.state |
See above | Object | Filterable field: crossproc_publisher_state |
CROSSPROC |
crossproc_reputation |
Carbon Black Cloud Reputation string for the crossproc. | String | CROSSPROC |
|
crossproc_target |
True if the process was the target of the cross-process event; false if the process was the actor | String | CROSSPROC |
|
device_external_ip |
IP address of the host as seen by the backend (the public IPv4 or IPv6 address used to contact the Carbon Black Cloud) | String | ENDPOINT STANDARD | COMMON |
device_group |
Sensor group to which the endpoint was assigned when the sensor recorded the event data | String | COMMON |
|
device_id |
Integer ID of the device that created this event | String | COMMON |
|
device_name |
Hostname of the device that created this event | String | COMMON |
|
device_os |
OS Type of device (Windows/OSX/Linux) | String | COMMON |
|
device_timestamp |
Time seen on sensor, based on sensor’s clock in RFC 3339 UTC format to seconds
Example: 2021-07-28 18:43:51 +0000 UTC |
ISO 8601 UTC timestamp | NOT FILTERABLE | COMMON |
event_description |
Long textual description of the event as seen in the Carbon Black Cloud web console | String | ENDPOINT STANDARD | |
event_id |
Internal Endpoint Standard event ID associated with this specific event — this event ID can be used to find the specific event in the Carbon Black Cloud web console | String |
NOT FILTERABLE
ENDPOINT STANDARD |
COMMON |
event_origin |
Indicates which product the event came from.
“EDR” indicates the event originated from Enterprise EDR. “NGAV” indicates the event originated from Endpoint Standard. |
String | COMMON |
|
fileless_scriptload_cmdline |
Deobfuscated script content run in a fileless context by the process | String | TOKENIZED | FILELESS SCRIPTLOAD |
fileless_scriptload_cmdline_length |
Character count of the deobfuscated script content run in a fileless context | String | FILELESS SCRIPTLOAD |
|
fileless_scriptload_hash |
SHA-256 hash(es) of the deobfuscated script content run by the process in a fileless context | String | FILELESS SCRIPTLOAD |
|
filemod_hash |
Cryptographic hashes of the file modified — this is represented as an array of two elements, MD5 and SHA-256 hash | String[] | FILEMOD |
|
filemod_name |
Full path to the file being modified on the device’s file system | String | FILEMOD |
|
local_ip |
IPv4 or IPv6 address in string format associated with the “local” end of this network connection | String | NETCONN |
|
local_port |
UDP/TCP port number associated with the “local” end of this network connection | String | NETCONN |
|
modload_count |
Count of modload events reported by the sensor since last initialization | Integer | MODULE LOAD |
|
modload_effective_reputation |
Effective reputation(s) of the loaded module(s); applied by the sensor when the event occurred | String | MODULE LOAD |
|
modload_hash |
MD5 or SHA-256 hash(es) of the module(s) loaded by the process | String[] | MODULE LOAD |
|
modload_md5 |
MD5 hash of the module loaded by the process | String | MODULE LOAD |
|
modload_name |
Full path to the module being loaded on the device’s file system | String | MODULE LOAD |
|
modload_publisher[]
.name |
Array with objects of two keys: “name” and “state”. Each array entry is a signature entry for the moduleload as reported by the endpoint | Object | Filterable field: modload_publisher |
MODULE LOAD |
modload_publisher[]
.state |
See above | Object | Filterable field: modload_publisher_state |
MODULE LOAD |
modload_sha256 |
SHA-256 hash of the module loaded by the process | String | MODULE LOAD |
|
v1.1.0
netconn_application_protocol |
Protocol detected in the application layer of the network session; does not always match port listed in IANA service registry | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_bytes_received |
Final byte count for all transport-layer payload received by the sensor’s endpoint during the session | Integer |
TOKENIZED
XDR |
NETCONN |
v1.1.0
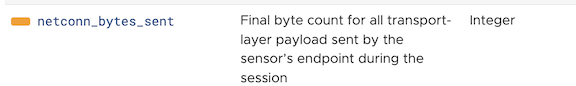
netconn_bytes_sent |
Final byte count for all transport-layer payload sent by the sensor’s endpoint during the session | Integer |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_community_id |
Community ID of the network session, calculated by this convention: https://github.com/corelight/community-id-spec | String |
TOKENIZED
XDR |
NETCONN |
netconn_domain |
DNS name associated with the “remote” end of this network connection — may be empty if the name cannot be inferred or the connection is made direct to/from a remote IP address | String | NETCONN |
|
v1.1.0
netconn_first_packet_timestamp |
Timestamp when the sensor detected the first packet in the network session | ISO 8601 UTC timestamp |
NOT FILTERABLE
XDR |
NETCONN |
netconn_inbound |
Set to true if the netconn is inbound | Boolean | NETCONN |
|
v1.1.0
netconn_ja3_local_fingerprint |
JA3 hash of the client side of the TLS session; JA3 if client-intiated, JA3s if server-initiated | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_ja3_local_fingerprint_fields |
Values used to calculate the JA3 hash for the local side of the TLS session | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_ja3_remote_fingerprint |
JA3 hash of the remote side of the TLS session; JA3 if client-intiated, JA3s if server-initiated | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_ja3_remote_fingerprint_fields |
Values used to calculate the JA3 hash for the remote side of the TLS session | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_last_packet_timestamp |
Timestamp when the sensor detected the last packet in the network session | ISO 8601 UTC timestamp |
NOT FILTERABLE
XDR |
NETCONN |
netconn_protocol |
String UDP or TCP protocol identifier | String
TCP, UDP |
NETCONN |
|
netconn_proxy_domain |
DNS name associated with the “proxy” end of this network connection — may be empty if the name cannot be inferred or the connection is made direct to/from a proxy IP address | String | NETCONN PROXY |
|
netconn_proxy_ip |
IPv4 or IPv6 address in string format associated with the “proxy” end of this network connection | String | NETCONN PROXY |
|
netconn_proxy_port |
UDP/TCP port number associated with the “proxy” end of this network connection | String | NETCONN PROXY |
|
v1.1.0
netconn_remote_device_id |
Carbon Black device ID (if sensor installed) of the remote side of the session | Integer |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_remote_device_name |
Carbon Black device name (if sensor installed) of the remote side of the session | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_request_headers |
HTTP request headers captured from start of HTTP session; represented as key:value pairs | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_request_method |
HTTP session request method | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_request_url |
URL requested for the HTTP session | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_response_headers |
HTTP response headers captured at start of HTTP session; represented as key:value pairs | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_response_status_code |
Status of requested HTTP operation | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_server_name_indication |
Hostname requested by TLS client to help server determine which certificate to use when multiple TLS-protected services are listening on the same IP:port binding | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_tls_certificate_issuer_name |
Certification authority that issued the X.509 certificate | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_tls_certificate_subject_name |
Subject that was issued the X.509 certificate | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_tls_certificate_subject_not_valid_after |
Timestamp when certificate expires | ISO 8601 UTC timestamp |
NOT FILTERABLE
XDR |
NETCONN |
v1.1.0
netconn_tls_certificate_subject_not_valid_before |
Timestamp when certificate becomes valid | ISO 8601 UTC timestamp |
NOT FILTERABLE
XDR |
NETCONN |
netconn_tls_cipher |
Set of cryptographic algorithms used to secure the TLS connection | String |
TOKENIZED
XDR |
NETCONN |
v1.1.0
netconn_tls_version |
TLS protocol version used in this session | String |
TOKENIZED
XDR |
NETCONN |
org_key |
The organization key associated with the console instance. Can be used to disambiguate events from different Carbon Black Cloud tenant organizations. | String | COMMON |
|
parent_cmdline |
Process command line associated with the parent process | String | TOKENIZED | COMMON |
parent_guid |
Unique ID of parent process. Please see this document for more information on how a process GUID is used and each of its components. | String | NOT FILTERABLE | COMMON |
parent_hash |
Cryptographic hashes of the executable file backing the parent process, represented as an array of two elements - MD5 and SHA-256 hash | String[] | COMMON |
|
parent_path |
Full path to the executable file backing the parent process on the device’s file system | String | COMMON |
|
parent_pid |
OS-reported Process ID of the parent process | String | COMMON |
|
parent_reputation |
Reputation of the parent process; applied when event is processed by the Carbon Black Cloud i.e. after sensor delivers event to the cloud | String | COMMON |
|
process_cmdline |
Command line executed by the actor process | String | TOKENIZED | COMMON |
process_duration |
The time difference in seconds between the process start and process terminate event | Integer | NOT FILTERABLE | COMMON |
process_fork_pid |
The PID of a process forked from the actor on *nix systems. If f process_pid != process_fork_pid, the current process was forked from original process_pid. | Integer | COMMON |
|
process_guid |
Unique ID of process. Please see this document for more information on how a process GUID is used and each of its components. | String | NOT FILTERABLE | COMMON |
process_hash |
Cryptographic hashes of the executable file backing this process, represented as an array of two elements - MD5 and SHA-256 hash | String[] | COMMON |
|
process_loaded_script_hash
DEPRECATED |
SHA-256 hash(es) of any script loaded from the filesystem through the duration of the process; compare with fileless_scriptload_hash | String[] |
ENDPOINT STANDARD
XDR |
SCRIPTLOAD |
process_loaded_script_name
DEPRECATED |
Filesystem path(s) of any script content loaded from the filesystem through the duration of the process; compare with fileless_scriptload_cmdline, scriptload_content | String |
ENDPOINT STANDARD
XDR |
SCRIPTLOAD |
process_path |
Full path to the executable file backing this process on the device’s file system | String | COMMON |
|
process_pid |
OS-reported Process ID of the current process | Integer | COMMON |
|
process_publisher[]
.name |
Array with objects of two keys: “name” and “state”. Each array entry is a signature entry for the process as reported by the endpoint | Object | Filterable field: process_publisher |
COMMON |
process_publisher[]
.state |
See above | Object | Filterable field: process_publisher_state |
COMMON |
process_reputation |
Reputation of the actor process; applied when event is processed by the Carbon Black Cloud i.e. after sensor delivers event to the cloud | String | COMMON |
|
process_terminated |
True if process was terminated; Always FALSE for Endpoint Standard events | Boolean | NOT FILTERABLE | COMMON |
process_username |
The username associated with the user context that this process was started under | String | COMMON |
|
regmod_name |
Full path to the registry key, including the hive, being modified on the Windows device’s registry | String | REGMOD |
|
remote_ip |
IPv4 or IPv6 address in string format associated with the “remote” end of this network connection | String | NETCONN |
|
remote_port |
UDP/TCP port number associated with the “remote” end of this network connection | String | NETCONN |
|
v1.1.0
version |
The schema version. The current schema version is “1.1.0”. This schema version will only be incremented if the field definitions are changed in a backwards-incompatible way. New fields in an event type or new event types will not result in a new schema version. | String | COMMON |
|
schema |
Not implemented | String | COMMON |
|
scriptload_content |
Deobfuscated script content (string, binary, or raw executable image) loaded from the filesystem at process launch; compare with fileless_scriptload_cmdline, process_loaded_script_name
Requires Windows CBC sensor 3.6 or later, AMSI support via Windows 10/Server version 1703 or later and Endpoint Standard product For more information see here |
String | ENDPOINT STANDARD | SCRIPTLOAD |
scriptload_content_length |
Character count of the deobfuscated filesystem script; compare with fileless_scriptload_cmdline_length
Requires Windows CBC sensor 3.6 or later, AMSI support via Windows 10/Server version 1703 or later and Endpoint Standard product For more information see here |
Integer | ENDPOINT STANDARD | SCRIPTLOAD |
scriptload_count |
Count of scriptload events across all processes reported by the sensor since last initialization | Integer | ENDPOINT STANDARD | SCRIPTLOAD |
scriptload_effective_reputation |
Effective reputation(s) of the loaded script(s); applied by the sensor when the event occurred
Requires Windows CBC sensor version 3.5 or later, macOS CBC sensor version 3.4 or later and Enterprise EDR ADAPTIVE_WHITE_LIST, ADWARE, COMMON_WHITE_LIST, COMPANY_BLACK_LIST, COMPANY_WHITE_LIST, HEURISTIC, IGNORE, KNOWN_MALWARE, LOCAL_WHITE, NOT_LISTED, PUP, RESOLVING, SUSPECT_MALWARE, TRUSTED_WHITE_LIST |
String | ENDPOINT STANDARD | SCRIPTLOAD |
scriptload_hash |
MD5 and/or SHA-256 hash(es) of the filesystem script file loaded at process launch | String | ENTERPRISE EDR | SCRIPTLOAD |
scriptload_name |
Filesystem path of script file(s) loaded at process launch | String |
ENTERPRISE EDR
XDR |
SCRIPTLOAD |
scriptload_publisher[]
.name |
Array with objects of two keys: “name” and “state”. Each array entry is a signature entry for the scriptload as reported by the endpoint
|
Object |
ENTERPRISE EDR
Filterable field: scriptload_publisher |
SCRIPTLOAD |
scriptload_publisher[]
.state |
See above | Object |
ENTERPRISE EDR
Filterable field: scriptload_publisher_state |
SCRIPTLOAD |
scriptload_reputation |
Reputation(s) of the loaded script(s); applied when event is processed by the Carbon Black Cloud i.e. after sensor delivers event to the cloud
Requires Windows CBC sensor version 3.5 or later, macOS CBC sensor version 3.4 or later and Enterprise EDR ADAPTIVE_WHITE_LIST, ADWARE, ``COMMON_WHITE_LIST, COMPANY_BLACK_LIST, COMPANY_WHITE_LIST, HEURISTIC, IGNORE, KNOWN_MALWARE, LOCAL_WHITE, NOT_LISTED, PUP, RESOLVING, SUSPECT_MALWARE, TRUSTED_WHITE_LIST |
String | ENTERPRISE EDR | SCRIPTLOAD |
sensor_action |
(optional) Included if the sensor blocked the event or terminated the application due to security policy
POLICY_NOT_APPLIED, ALLOW, ALLOW_AND_LOG, TERMINATE, DENY |
String | XDR | COMMON |
target_cmdline |
The command line that was executed to create the process represented in the childproc properties. | String | TOKENIZED | COMMON |
type |
The event type. Use this field to determine which fields should be expected per the Event Type column of this table. | String | COMMON |
Data Samples
{
"type": "endpoint.event.procstart",
"process_guid": "ABCD1234-006e8d46-00001310-00000000-1d5fd46cc37d700",
"parent_guid": "ABCD1234-006e8d46-00000290-00000000-1d5fa5dbbaa12ce",
"backend_timestamp": "2020-03-25 22:38:54 +0000 UTC",
"org_key": "ABCD1234",
"device_id": "7245126",
"device_name": "cbc-win10",
"device_external_ip": "9.8.7.6",
"device_os": "WINDOWS",
"device_group": "Windows Group",
"action": "ACTION_CREATE_PROCESS",
"schema": 1,
"event_description": "The application \"<share><link hash=\"0f407d7194e7955e312b177b16cc409ac89b4d0494c60ce75469fd4c474d4043\">C:\\program files (x86)\\google\\chrome\\application\\chrome.exe</link></share>\" invoked the application \"<share><link hash=\"0f407d7194e7955e312b177b16cc409ac89b4d0494c60ce75469fd4c474d4043\">C:\\program files (x86)\\google\\chrome\\application\\chrome.exe</link></share>\". ",
"alert_id": "WXYZ0987",
"event_id": "54885ebc6ee911eabc70416f8358e4f2",
"device_timestamp": "2020-03-25 22:38:03.353 +0000 UTC",
"process_terminated": false,
"process_reputation": "REP_RESOLVING",
"parent_reputation": "",
"process_pid": 4880,
"parent_pid": 656,
"process_publisher": [
{
"name": "Google Inc",
"state": "FILE_SIGNATURE_STATE_SIGNED | FILE_SIGNATURE_STATE_VERIFIED | FILE_SIGNATURE_STATE_TRUSTED"
}
],
"process_path": "c:\\program files (x86)\\google\\chrome\\application\\chrome.exe",
"parent_path": "c:\\windows\\system32\\services.exe",
"process_hash": [
"3623a0e7cdcf3310ffb4c87c5b43ae02",
"0f407d7194e7955e312b177b16cc409ac89b4d0494c60ce75469fd4c474d4043"
],
"parent_hash": [
"db896369fb58241adf28515e3765c514",
"a2e369df26c88015fe1f97c7542d6023b5b1e4830c25f94819507ee5bcb1dfcc"
],
"process_cmdline": "\"C:\\Program Files (x86)\\Google\\Chrome\\Application\\chrome.exe\" --flag-switches-begin --flag-switches-end --enable-audio-service-sandbox",
"parent_cmdline": "",
"process_username": "CBC-WIN10\\user",
"sensor_action": "ALLOW",
"event_origin": "NGAV",
"childproc_name": "c:\\program files (x86)\\google\\chrome\\application\\chrome.exe",
"childproc_hash": [
"3623a0e7cdcf3310ffb4c87c5b43ae02",
"0f407d7194e7955e312b177b16cc409ac89b4d0494c60ce75469fd4c474d4043"
],
"target_cmdline": "\"C:\\Program Files (x86)\\Google\\Chrome\\Application\\chrome.exe\" --type=utility --field-trial-handle=1656,13710686576560040528,13403776044656688818,131072 --lang=en-US --service-sandbox-type=utility --enable-audio-service-sandbox --mojo-platform-channel-handle=5236 --ignored=\" --type=renderer \" /prefetch:8"
}{
"version": "1.1.0",
"type": "endpoint.event.netconn",
"process_guid": "ABCD1234-011df811-00000820-00000000-1da2d773b7d0f2e",
"parent_guid": "ABCD1234-011df811-000002b4-00000000-1da2d7738407692",
"backend_timestamp": "2023-12-15 05:58:20 +0000 UTC",
"org_key": "ABCD1234",
"device_id": "12345678",
"device_name": "DEMO-MACHINE",
"device_external_ip": "1.2.3.4",
"device_os": "WINDOWS",
"action": "ACTION_CONNECTION_CREATE",
"schema": 1,
"device_timestamp": "2023-12-15 05:56:16.0222142 +0000 UTC",
"process_terminated": false,
"process_reputation": "REP_WHITE",
"parent_reputation": "REP_WHITE",
"process_pid": 2080,
"parent_pid": 692,
"process_publisher": [
{
"name": "Microsoft Windows Publisher",
"state": "FILE_SIGNATURE_STATE_SIGNED | FILE_SIGNATURE_STATE_VERIFIED | FILE_SIGNATURE_STATE_TRUSTED | FILE_SIGNATURE_STATE_OS"
}
],
"process_path": "c:\\windows\\system32\\svchost.exe",
"parent_path": "c:\\windows\\system32\\services.exe",
"process_hash": [
"145dcf6706eeea5b066885ee17964c09",
"f13de58416730d210dab465b242e9c949fb0a0245eef45b07c381f0c6c8a43c3"
],
"parent_hash": [
"e606e7e0d5e94af8222715a24df0776b",
"43ec773e0ec626bf6d8a7fd04e64dc36afa6801444a3c36ef4da2a909fa0d83f"
],
"process_cmdline": "C:\\WINDOWS\\system32\\svchost.exe -k NetworkService -p -s Dnscache",
"parent_cmdline": "C:\\WINDOWS\\system32\\services.exe",
"process_username": "NT AUTHORITY\\NETWORK SERVICE",
"sensor_action": "ACTION_ALLOW",
"event_origin": "EDR",
"remote_port": 5353,
"remote_ip": "9.8.7.6",
"local_port": 5353,
"local_ip": "4.5.6.7",
"netconn_inbound": true,
"netconn_protocol": "PROTO_UDP",
"netconn_community_id": "1:PYzPIo/Fb8XKxwx1HmwapOPOMr4="
}{
"version": "1.1.0",
"type": "endpoint.event.moduleload",
"process_guid": "ABCD1234-0120b1e3-00001e78-00000000-1da2f2349b8c999",
"parent_guid": "ABCD1234-0120b1e3-000002e8-00000000-1da2d8f7a6c44d1",
"backend_timestamp": "2023-12-15 06:59:39 +0000 UTC",
"org_key": "ABCD1234",
"device_id": "18919907",
"device_name": "DEMO-DEVICE",
"device_external_ip": "9.8.7.6",
"device_os": "WINDOWS",
"action": "ACTION_LOAD_MODULE",
"schema": 1,
"device_timestamp": "2023-12-15 06:52:36.8474656 +0000 UTC",
"process_terminated": false,
"process_reputation": "REP_WHITE",
"parent_reputation": "REP_WHITE",
"process_pid": 7800,
"parent_pid": 744,
"process_publisher": [
{
"name": "Microsoft Windows Publisher",
"state": "FILE_SIGNATURE_STATE_SIGNED | FILE_SIGNATURE_STATE_VERIFIED | FILE_SIGNATURE_STATE_TRUSTED | FILE_SIGNATURE_STATE_OS"
}
],
"process_path": "c:\\windows\\system32\\svchost.exe",
"parent_path": "c:\\windows\\system32\\services.exe",
"process_hash": [
"145dcf6706eeea5b066885ee17964c09",
"f13de58416730d210dab465b242e9c949fb0a0245eef45b07c381f0c6c8a43c3"
],
"parent_hash": [
"e606e7e0d5e94af8222715a24df0776b",
"43ec773e0ec626bf6d8a7fd04e64dc36afa6801444a3c36ef4da2a909fa0d83f"
],
"process_cmdline": "C:\\WINDOWS\\system32\\svchost.exe -k wsappx -p -s AppXSvc",
"parent_cmdline": "C:\\WINDOWS\\system32\\services.exe",
"process_username": "NT AUTHORITY\\SYSTEM",
"sensor_action": "ACTION_ALLOW",
"event_origin": "EDR",
"modload_name": "c:\\windows\\system32\\appxdeploymentserver.dll",
"modload_count": 0,
"modload_effective_reputation": "REP_ADAPTIVE",
"modload_hash": [
"5f6d81c3912a99a429c45dd0ef45b9aa",
"6f02ff703ebee246c21d306ad72710406029b544e38271916165abf0b7ce4532"
],
"modload_md5": "5f6d81c3912a99a429c45dd0ef45b9aa",
"modload_publisher": [
{
"name": "Microsoft Windows",
"state": "FILE_SIGNATURE_STATE_SIGNED | FILE_SIGNATURE_STATE_VERIFIED | FILE_SIGNATURE_STATE_TRUSTED | FILE_SIGNATURE_STATE_OS | FILE_SIGNATURE_STATE_CATALOG_SIGNED"
}
],
"modload_sha256": "6f02ff703ebee246c21d306ad72710406029b544e38271916165abf0b7ce4532"
}Last modified on July 23, 2024