Deprecated Versions: Apps for ServiceNow - Installation and Configuration
This is for deprecated App Versions; SecOps v2.1.0, ITSM v2.1.0, VR v1.1.0.
Please see the latest Installation and Configuration Guide for current versions of the apps.
Overview
To integrate Carbon Black Cloud and ServiceNow, there are three apps available for different use cases.
- To manage security incidents, there is a SecOps App and an ITSM App; these have the same functionality and the choice is determined by whether you have the SecOps or ITSM ServiceNow module.
- To manage vulnerabilities identified by Carbon Black Cloud, the Vulnerability Response (VR) app canl ingest vulnerabilities from Carbon Black Cloud into ServiceNow. It can be used alone or in combination with one of the other apps.
All of these apps will install the necessary prerequisites including the VMware Carbon Black Cloud Base Connector App for ServiceNow. This takes care of the connectivity between ServiceNow and Carbon Black Cloud to collect alerts from Carbon Black Cloud and store them in the Alerts table in ServiceNow, populate the ServiceNow CMDB with Carbon Black Cloud Device information and enable actions to be initiated in ServiceNow and execute in Carbon Black Cloud.
Getting Started
The configuration guide describes:
- Prerequisites - decisions to be made prior to installation
- Installation - install the Apps from the ServiceNow App Store
- Configuration of API Access in Carbon Black Cloud
- Configuration of Role and Users in ServiceNow
- Configuration of the Apps - create a profile to ingest data to ServiceNow
- Troublshooting and Known Issues - updates to the apps
- Release Notes - updates to the apps
Prerequisites
-
Access to Carbon Black Cloud
-
Access to ServiceNow
- Rome, SanDiego and Tokyo are the supported versions.
- ServiceNow ITSM or ServiceNow SecOps
-
Determine whether you will use the ITSM or SecOps app; this will align to the ServiceNow module you are licensed for.
-
Determine whether you will get alerts from Carbon Black Cloud using the Alerts REST API or from an AWS S3 Bucket using the Carbon Black Cloud Data Forwarder.
- The REST API is easier to set up, requiring only API credentials to be entered into ServiceNow. ServiceNow will then poll Carbon Black Cloud for new Alerts.
- The Data Forwarder is recommended when you have a high volume or significant bursts of data as it provides improved
scalability for large volumes of data. It requires
- A Data Forwarder to be configured in Carbon Black Cloud which will write to an AWS S3 Bucket owned by you; and
- A ServiceNow MID server to ingest the data.
-
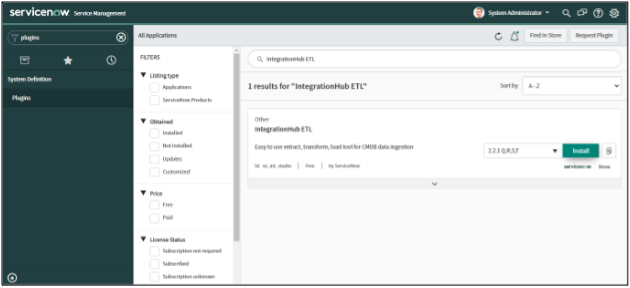
If you are ingesting Assets (Devices) from Carbon Black Cloud to the ServiceNow CMDB, install the IntegrationHub ETL .
To install this plugin:
1. Log in to your ServiceNow instance with your user credentials.
2. Verify you have the system administrator (admin) role.
3. Navigate to System Definition > Plugins in your instance.
4. Search for and install the IntegrationHub ETL plugin.
-
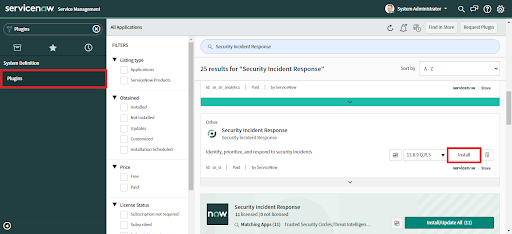
If you are using the SecOps module, then install and configure the Security Incident Response plugin.
The SecOps App requires the following plugins:
• Security Incident Response
To install these plugins:
1. Log in to your instance with your user credentials.
2. Verify you have the system administrator (admin) role.
3. Navigate to System Definition > Plugins in your instance.
4. Search for and install each plugin.
-
If you are using the SecOps module, or if you are using the ITSM module and want to use SOAR actions that store files, then install the Threat Intelligence plugin.
Install the Threat Intelligence plugin to:
• use the MITRE features in the SecOps module.
• use "Download Binary from UBS" or "Get File on Asset" SOAR actions.
1. Prerequisite: Threat Intelligence plugin has been installed - see earlier step
2. Navigate to TAXII profile
3. Click on MITRE ATT&CK®
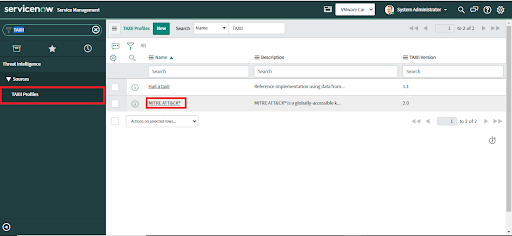
4. Click on "Enterprise ATT&CK" in MITRE ATT&CK®’s TAXII Collections table
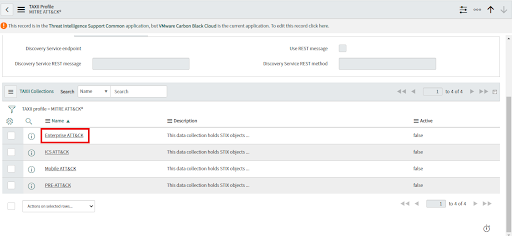
5. Click on Integration Runs.
6. Select the Number of Integration Runs you want to execute. If Integration Run is empty then click on New to Create a New Integration Run and then click on Process.
7. Click on Execute Now.
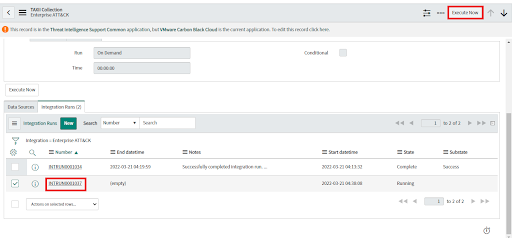
8. Wait until the state changes to "complete".
-
Decide whether to use the Vulnerability Response Application
To use the VMware Carbon Black Cloud Vulnerability Response App, the ServiceNow Vulnerability Response plugin is required.
• Log in to your instance with your user credentials.
• Verify you have the system administrator (admin) role.
• Navigate to System Definition > Plugins in your instance.
• Search and install the plugin, developed by ServiceNow.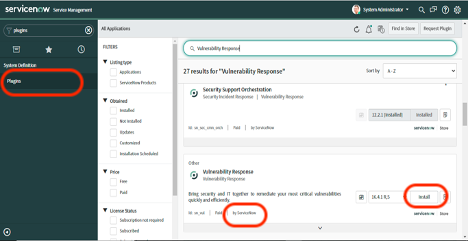
-
Activate Extensions
The Domain Support - Domain Extensions Installer ServiceNow plugin must be activated to enable multitenancy support.
To activate the plugin:
1. Sign in to your instance email account at https://support.servicenow.com.
2. From My Instance, under Instance Action, select Activate Plugin.
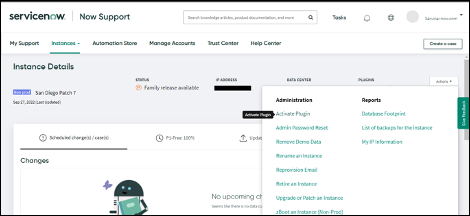
3. Search for plugin "Domain Separation Center" and click Activate > Activate plugin.
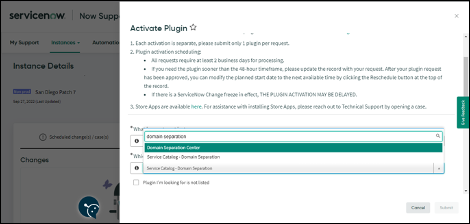
4. When you click on "Activate plugin", a request is sent for plugin activation. Once the Plugin is activated, you will receive a notification email.
5. To fetch Vulnerabilities or Vulnerable Items with domain separation the user has to complete script changes as specified in the ServiceNow documentation Create domain-separated imports for a Vulnerability Response or Application Vulnerability Response Integration.
6. Now that the plugin is activated on the instance, you can install the application.
Optional: Set up the Data Forwarder and MID server
Setting up the Data Forwarder and Mid Server described in this section is only needed if you choose to use the Data Forwarder and AWS S3 Bucket option above. Data collection through REST API does not require these steps.
Full details about the Carbon Black Cloud Data Forwarder and options to configure it are in the
Carbon Black Cloud User Guide.
The steps included here are a summary with the essential options.
1. Create an AWS S3 Bucket.
2. Configure the bucket policy to receive data from Carbon Black Cloud.
2. Configure the Access policy. Replace the tokens with your own values.
{
"Version": "2008-10-17",
"Id": "__default_policy_ID",
"Statement": [
{
"Sid": "__sender_statement",
"Effect": "Allow",
"Principal": {
"Service": "s3.amazonaws.com"
},
"Action": "SQS:SendMessage",
"Resource": "arn:aws:sqs:<aws-region>:<AWS Account Number>:<name-of-queue>",
"Condition": {
"ForAllValues:ArnEquals": {
"aws:SourceArn": "arn:aws:s3:::<name-of-s3-bucket>"
}
}
}
]
}
Note: If you need to reload older events and are using SQS to pull buckets, the events will not be available in the queue once they are retrieved. To view historical events or reload data, copy the events to another prefix to copy it to the queue.
Install the Apps
There are three apps available:
- If you want incidents to be created from Alerts then choose either ITSM App or the SecOps App. The one you install will depend on whether you have the ITSM or SecOps module in ServiceNow.
- If you want vulnerability information from Carbon Black Cloud then install the Vulnerability Response app. This can be used alone or in combination with the ITSM or SecOps Apps.
Installation requires either: ServiceNow System Administrator Role which includes permissions for the following actions:
- Installation of the integration application plugins
- Mid_server to configure data ingest from an AWS S3 bucket
- Read, write and delete any record
- Execute all the SOAR actions
- View Application Logs
- Access Support Contact
- Uninstall Application.
Or the VMware CBC Admin (x_vmw_cb_connector.admin) role
- This will only be available if it has been configured during a previous installation of a Carbon Black Cloud app.
• VMware Carbon Black Cloud for IT Service Management
• VMware Carbon Black Cloud for Security Operations
• VMware Carbon Black Cloud for Vulnerability Response
1. Log in to the ServiceNow instance on which you want to install the application.
1. Navigate to System Applications > All Available Applications > All
1. Click the Not Installed tab. A list of applications available for installation will be displayed.
1. Locate the VMware Carbon Black Cloud ITSM, SecOps or Vulnerability Response app, select it, and click Install.
1. The application will be installed on your instance.
Note: One Integration Instance is provided out-of-the box. If data is only being ingested from a single Carbon Black Cloud Organization, this step can be skipped.
The default integration instance is named “VMware Carbon Black Cloud VR Integration”. This can be used for the first Configuration Profile. Every subsequent Configuration Profile will require its own dedicated Integration instance. This is most commonly required when multitenancy features are required for ingesting data from multiple Carbon Black Cloud organizations.
1. Login to the ServiceNow instance.
2. Navigate to VMware Carbon Black Cloud > Integration Instances.
3. One default integration instance named "VMWare CBC VR Integration" will be available.
4. New Integration Instances can be created by clicking on the "New" button.
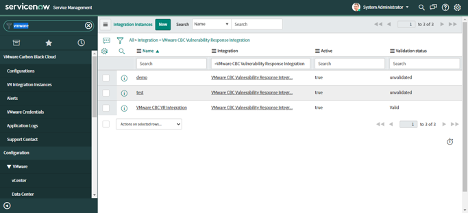
5. Enter the name of the Integration Instance and click on the "Submit" button. Integration Instance will be created and Integration will be created automatically.
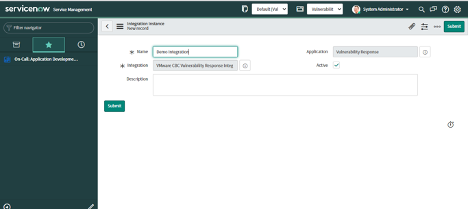
6. Users can view the created Integration by clicking on VMware Carbon Black Cloud -> Integration.
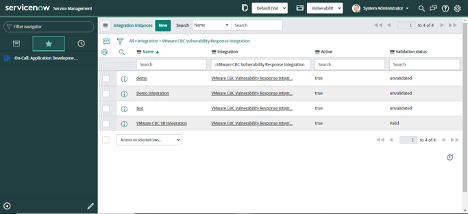
This will be used when configuring the profile.
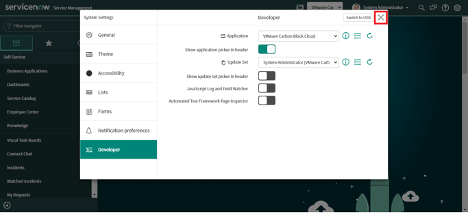
1. Click on "Settings".
2. Click on "Developer" under System Settings on the left
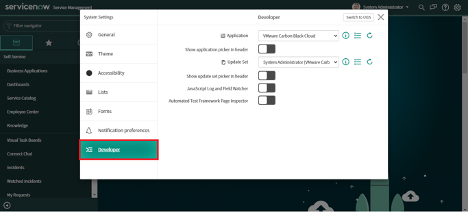
3. Select "VMware Carbon Black Cloud" in the Application picker.
4. Enable "Show application picker in header".
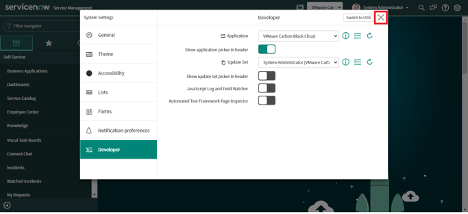
5. Click on X (Cross) to close the popup.
Configure API Access
ServiceNow requires an API key with the appropriate permissions to make the API calls. Create the key in Carbon Black Cloud.
Get your Org Key from Carbon Black Cloud on the General > Settings page.
Get the Carbon Black Cloud Hostname from the Authentication Page or the URL when you are logged in to the Carbon Black Cloud console.
For example, https://dashboard.confer.net
The ITSM and SecOps Apps support the same actions.
Note: SOAR Actions are available based on their availability in the sensors deployed and the permissions configured for the API credentials.
| ServiceNow Action | Notation Name | Permissions |
|---|---|---|
| Configuration Profile - Create/Update/Delete | org.alerts | READ |
| Configuration Profile - Asset Inventory Ingest | device | READ |
| Alert Filtering - Create/Update/Delete | org.alerts | READ |
| Incident Creation - Create/Update/Delete | org.alerts | READ |
| Field Mapping - Create/Update/Delete | org.alerts | READ |
| Scheduling - Create/Update/Delete | org.alerts | READ |
| Alert Ingestion - Update | org.alerts | READ |
| Bi Directional Sync | org.alerts | READ |
| Close Incident and alert Dismissal | org.alerts.close | EXECUTE |
| Manual Alert Dismissal | org.alerts.close | EXECUTE |
| Ban / Unban process hash | org.reputations | CREATE |
| Get File from Asset | device, org.liveresponse.session ; org.liveresponse.file | device: READ ; org.liveresponse.session: CREATE, READ, DELETE ; org.liveresponse.file: READ |
| Put File on Asset | device, org.liveresponse.session ; org.liveresponse.file | device: READ ; org.liveresponse.session: CREATE, READ, DELETE ; org.liveresponse.file: CREATE, READ |
| Delete File from Endpoint | org.liveresponse.session ; org.liveresponse.file | org.liveresponse.session: CREATE, READ, DELETE ; org.liveresponse.file: READ, DELETE |
| Dismiss Alerts | org.alerts.close | EXECUTE |
| Get Process Metadata | org.search.events | CREATE, READ |
| Get Binary Metadata from UBS | ubs.org.sha256 | READ |
| Get Endpoint (Asset) Information | device | READ |
| Get Enriched Events | org.search.events | CREATE, READ |
| Get Running Processes | org.liveresponse.session ; org.liveresponse.process | org.liveresponse.session: CREATE, READ, DELETE ; org.liveresponse.process: READ |
| Update Endpoint (Asset) Policy | device.policy | UPDATE |
| Quarantine / Unquarantine Endpoint | device.quarantine | EXECUTE |
| Kill process on an endpoint | org.liveresponse.session ; org.liveresponse.process | org.liveresponse.session: CREATE, READ, DELETE ; org.liveresponse.process: READ, DELETE |
| Add or remove an IoC to or from a Feed | org.feeds | CREATE, UPDATE |
| Download Binary from UBS | ubs.org.file | READ |
| Enable/Disable Asset Bypass | device.bypass | EXECUTE |
| Get Process Executions by Hash | org.search.events | READ, CREATE |
| Ignore an IOC | org.watchlists | UPDATE |
| Add a note to an Alert | org.alerts.notes | CREATE |
| Get Directory Information | device ; org.liveresponse.session ; org.liveresponse.file | device READ ; org.liveresponse.session CREATE, READ, UPDATE, DELETE ; org.liveresponse.file READ |
| Get Registry Key Information On Asset | device ; org.liveresponse.session | org.liveresponse.registry: READ ; device READ ; org.liveresponse.session: CREATE, READ, UPDATE, DELETE ; org.liveresponse.registry: READ |
| Manage Registry Key Information | device ; org.liveresponse.session ; org.liveresponse.registry | device: READ ; org.liveresponse.session: CREATE, READ, UPDATE, DELETE ; org.liveresponse.registry: CREATE, READ, UPDATE, DELETE |
| Get External Device Information | external-device.manage | READ |
| Dismiss Future Alerts | org.alerts.close | EXECUTE |
| Submit Live Query Run | livequery.manage | CREATE, READ |
| Approve an external USB device | external-device.manage | CREATE |
| Get/Approve/Reject Alert Recommendation | org.recommendations | CREATE, READ, DELETE |
| Execute a Custom Script on the Endpoint | device ; org.liveresponse.session ; org.liveresponse.process | device: READ ; org.liveresponse.session: CREATE, READ, UPDATE, DELETE ; org.liveresponse.process: EXECUTE |
The Vulnerability Response App Requires the following permissions for data ingest:
| ServiceNow Action | Notation Name | Permissions |
|---|---|---|
| Configuration Profile - Create/Update/Delete | vulnerabilityAssessment.data | READ |
| Configuration Profile - Asset Inventory Ingest | device | READ |
| Ingest Vulnerability Data | vulnerabilityAssessment.data | READ |
| Ingest Device Data | device | READ |
In Carbon Black Cloud:
- Create a custom access level with the required permissions from the previous table.
- Create an API Key of type Custom and assign the Access Level created in the previous step.
See Authentication for details about API Keys in Carbon Black Cloud.
Configure Roles and Users
There are two application specific roles to be configured in ServiceNow; one with the privileges to administer the apps and one for analysts.
After these roles have been configured, grant them to users.
- The built in Service Now System Administrator role grants users with that role the permissions to:
- Install the integration application plugins
- Configure Data Collection using the Data Forwarder with AWS S3 Bucket
- Read, write and delete any record
- Create Users
- Can execute all SOAR actions
- View Application Logs
- Access Support Contact
- Uninstall the Application
1. Navigate to the Roles Page in the ServiceNow search menu on the left.
2. Find and open the role `x_vmw_cb_connector.admin`.
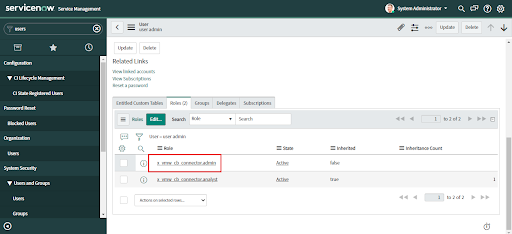
3. Scroll down and click on the "Edit" button. If the “Edit” button is not visible then add the scope of the application.
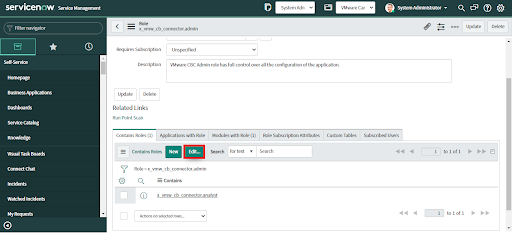
4. Search for the roles to be added. For each role select the role and move it to `Contains Roles List` by either double-clicking on the role or clicking on the right arrow.
To VMware CBC Admin (x_vmw_cb_connector.admin) add the roles:
• itil
• itil_admin
• mid_server - for selecting the mid server to ingest data from the AWS S3 Bucket. Only required if configuring the Data Forwarder.
• flow_operator
• workflow_admin
• n_ti.malicious_attachment_access (to download and view secured attachments)
• sn_ti.observable.write (to view and edit observable records)
Which will grant users with that role the permissions to
• Install the integration application plugins
• Create Users
• Configure the application for REST API approach or Data Forwarder with AWS S3 Bucket approach
• View Application Logs
• Manually create an Incident from Alerts
• Configure automatic creation of an Incident from Alerts
• Manually dismiss an Alert
• Close Incidents
• Perform SOAR actions
• Bi Directional Sync of Alerts in ServiceNow and Carbon Black Cloud
• Access Support Contact.
5. Repeat steps two to four to add the following roles to VMware CBC Analyst (x_vmw_cb_connector.analyst):
• itil
• itil_admin
• flow_operator
• n_ti.malicious_attachment_access (to download and view secured attachments)
• sn_ti.observable.write (to view and edit observable records)
Which will grant users with that role the permissions to
• Access the Application
• Manually create an Incident from Alerts
• Manually dismiss an Alert
• Close Incidents
• Perform SOAR actions
• Bi Directional Sync of Alerts in ServiceNow and Carbon Black Cloud
• Access Support Contact.
1. Navigate to the Roles Page in the ServiceNow search menu on the left.
2. Edit the following bundled roles, by searching for the bundled roles and then selecting Contains Role > Edit
3. To VMware CBC Admin (x_vmw_cb_connector.admin) add the roles:
• sn_si_admin
• export_set_scheduler
• mid_server (to configure Data Forwarder Alert ingest)
• sn_ti.malicious_attachment_access (to download and view secured attachment)
• sn_ti.observable.write (to view and edit observable records)
Which will grant users with that role the permissions to
• Install the integration application plugins
• Create Users
• Configure the application for REST API approach or Data Forwarder with AWS S3 Bucket approach
• View Application Logs
• Manually create a Security Incident from Alerts
• Configure automatic creation of an Incident from Alerts
• Manually dismiss an Alert
• Close Incidents
• Perform SOAR action on Alerts
• Apply MITRE Classification
• Access Support Contact.
4. To VMware CBC Analyst (x_vmw_cb_connector.analyst) add the roles:
• sn_si_analyst
• export_set_scheduler
• sn_ti.malicious_attachment_access (to download and view secured attachment)
• sn_ti.observable.write (to view and edit observable records)
Which will grant users with that role the permissions to
• Access the Application
• Manually create an Incident from Alerts
• Manually dismiss an Alert
• Close Incidents
• Perform SOAR action on Alerts
• Apply MITRE Classification
• Access Support Contact.
Note: sn_vul.vulnerability_admin contains x_vmw_cb_connector.admin role.
Images for each step are included in the ITSM roles configuration above.
1. Navigate to the Roles Page in the ServiceNow search menu on the left.
2. Edit the following bundled roles, by searching for the bundled roles and then selecting Contains Role > Edit
3. To VMware CBC Admin (x_vmw_cb_connector.admin) add the roles:
• sn_vul.vulnerability_admin
Which will grant users with that role the permissions to
• Can read, write, update and delete any record in the Configuration Profiles.
• Can read, write, update and delete any record in the Vulnerability Profiles.
• Can read, write, update and delete any record in the Integration Instances.
• Can read, write, update and delete any record in the Vulnerable Item
• View Application Logs
• Access Support Contact.
4. To VMware CBC Analyst (x_vmw_cb_connector.analyst) add the roles:
• sn_vul.read_all
Which will grant users with that role the permissions to
• Can read the records of Configurations
• Can read the records of Vulnerable Item
• Access Support Contact.
User management requires the System Administrator role.
To create a User:
1. Navigate to Organization > Users.
2. Click the Users module.
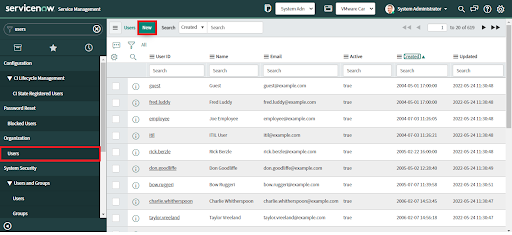
3. Above the User ID list, click on the "New" button. A new User form displays.
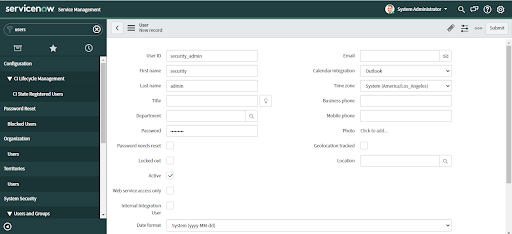
4. Fill in the form.
• User ID - Unique User ID for the role in the current ServiceNow Platform instance.
• First Name - First Name of the user being created
• Last Name - Last Name of the user being created
• Title - Job Title, for example, Security User
• Password - Unique password created for this user
• Email - Unique email address
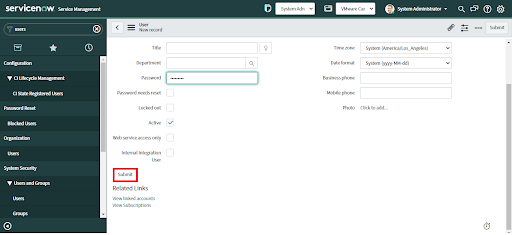
5. Click "Submit." Now the user has been created. See the next section to assign roles.
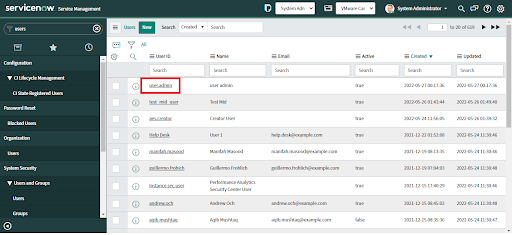
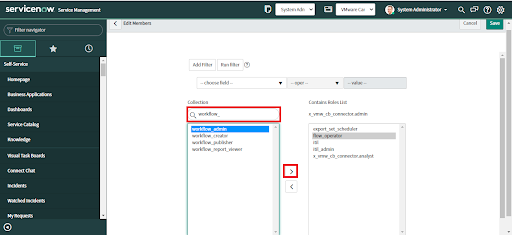
2. Once the record is open, scroll down and go to the Roles tab, and click "Edit".
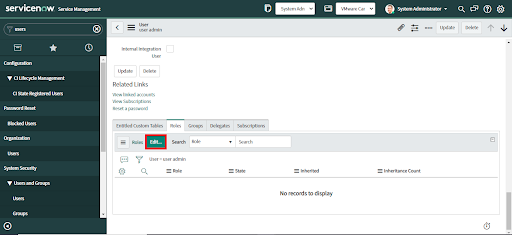
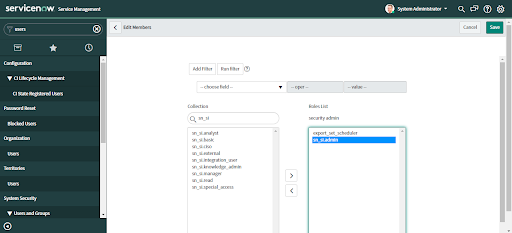
3. When the Edit Members form displays, select the required roles from the Collection and move it to the Roles list.
• Assign x_vmw_cb_connector.admin for Administrators of the Carbon Black Cloud app. Users with this role can configure the applications as well as do everything an analyst can.
• Assign x_vmw_cb_connector.analyst for other users of the Carbon Black Cloud app. Users with this role can create tickets and perform actions in the integration, and are limited to viewing configuration.
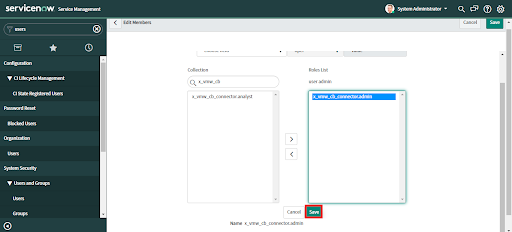
4. Click save
Configure a Profile
A profile is required to control the rules for ingestion of data and incident creation.
To configure a new profile the role VMware CBC admin is required.
1. Login to the ServiceNow instance
2. Navigate to VMware Carbon Black Cloud > Configurations.
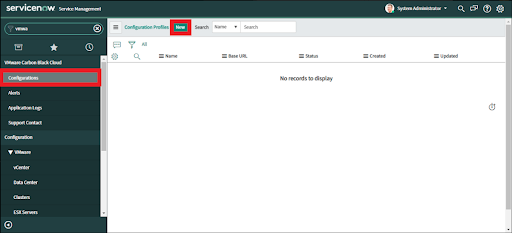
3. Click on the "New" button to create a Configuration Profile.
4. Enter a unique "Name", "Order", and "Description" in the Overview section.
• Multiple values in the order field of profile configuration can be added using space between each integer.
5. Select the apps that you want to configure.
• Vulnerability Response (Carbon Black Cloud VR) can be used alone or with the ITSM or SecOps App.
• Only one of "Carbon Black Cloud ITSM" or "Carbon Black Cloud SecOps" can be selected.
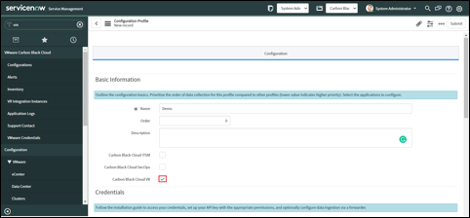
Enter the following information in the Credentials section:
• Carbon Black Cloud URL (this is the Hostname, for example
https://defense.conferdeploy.net)
• Org Key
• API ID
• API Secret Key
These are the values obtained from Carbon Black Cloud in the earlier Configure API Access in Carbon Black Cloud section.
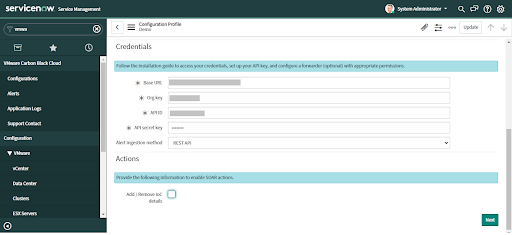
• For Alert Ingestion Approach, choose Data Forwarder / AWS S3 Bucket.
• Additional fields will display below the dropdown field.
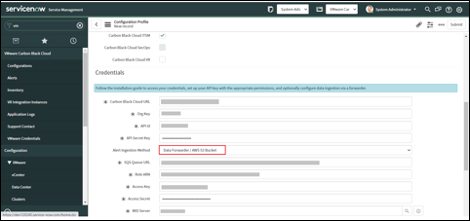
• Populate the following fields with information from the earlier section, Set up the Data Forwarder and Mid Server.
○ SQS Queue URL
○ Role ARN
○ Access Key
○ Access Secret
○ Select a Validated and Up MID server from the MID server field.
• To ingest alerts from AWS S3 Bucket, the application scope must be “VMware Carbon Black Cloud”. If the application scope is other than “VMware Carbon Black Cloud” then alerts will not be ingested from AWS S3 Bucket. See Install the Apps for more information.
• Based on the amount of data consumed from the SQS Queue, the user can configure the
○ MID server JVM Memory size from Set the MID Server JVM memory size
○ Number of MID server threads from Set MID Server Thread Use
Note: Alerts from the S3 bucket will get ingested into ServiceNow even if those alerts have a different org_key than that of the configured profile.
• Click the "Next" button to advance to the next tab.
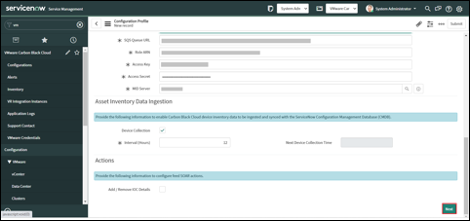
• Enter the frequency of collection in hours
• The Next Collection Time will populate after the first collection runs.
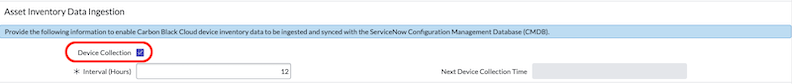
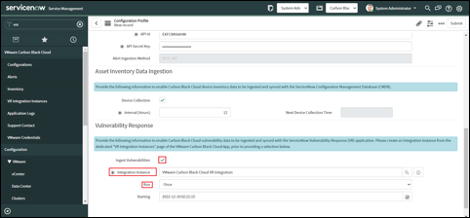
• Enable "Ingest Vulnerabilities"
• Select the Integration Instance in the "Integration Instance" field.
• Configure the frequency that the vulnerabilities from the Carbon Black Cloud should be ingested into ServiceNow from the "Run" field.
• If only the Vulnerability Response App is being configured, click on the "Finish" button to save the record. Otherwise continue the configuration wizard.
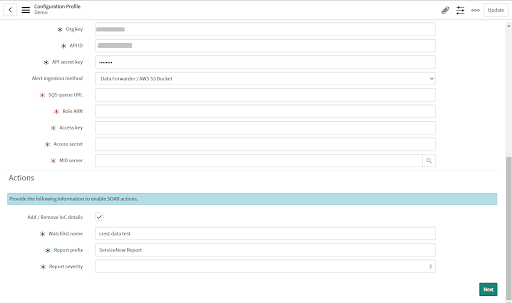
To configure the action `Add IOC to Feed` check the "Add/Remove IoC details" checkbox to enable the configuration fields.
Provide the following fields:
• Watchlist name: Provide the name of any existing classifier watchlist or provide a new name for the watchlist.
If the watchlist specified does not exist, the application will create it.
If the watchlist exists but is not valid then it will raise the following error: "Watchlist must be empty or subscribed to a Feed".
• Report prefix: Provide the prefix for the report to be created to add the IOCs to it.
• Report severity: Specify the report severity.
Click the "Next" button to advance to the next tab.
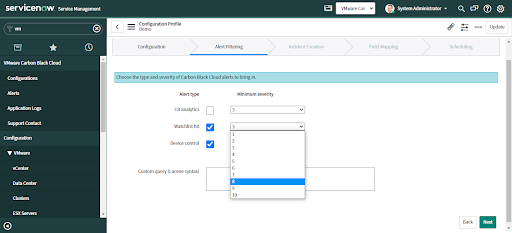
Three types of alerts are supported for ingestion into ServiceNow, depending on which Carbon Black Cloud products are enabled:
• CB Analytics Alerts
• Device Control Alerts
• Watchlist Alerts
Note: Alert Filtering is only supported when Alerts are ingested using the API. It is not supported for the Data Forwarder Ingestion method.
To change this configuration after the initial setup, navigate to VMware Carbon Black Cloud > Configurations and click on “Alert Filtering”.
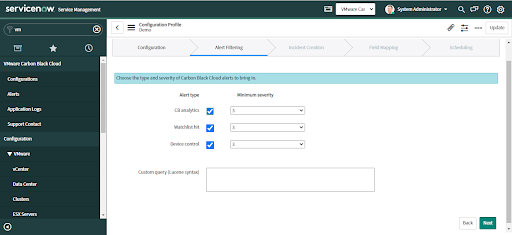
• Uncheck any alert types you do not want to ingest from Carbon Black Cloud.
• Select the Minimum severity from 1-10. By default, the value is 3 for each Alert type.
• Optional: For more granular control of alert filtering, use the Custom Query field to query for a specific set of alert criteria.
To change this configuration after the initial setup, navigate to VMware Carbon Black Cloud > Configurations and click on "Incident Creation".
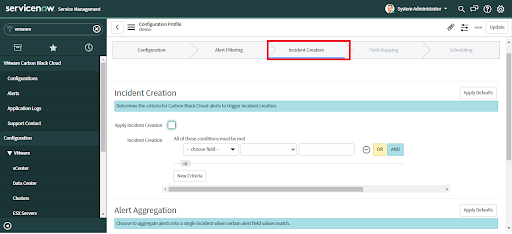
• An automatic incident will be created only if the "Apply Incident Creation" checkbox has been checked and the condition given in the Incident Creation field has been satisfied.
• Click on the "Apply Defaults" button to get a suggested default value for any settings.
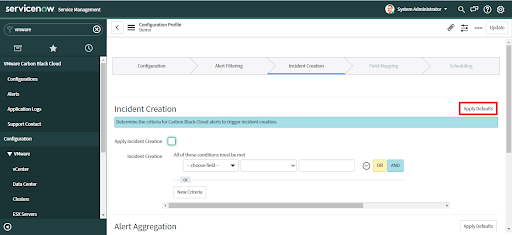
• Check the default values to verify that the settings are what you desire for Incident Creation criteria.
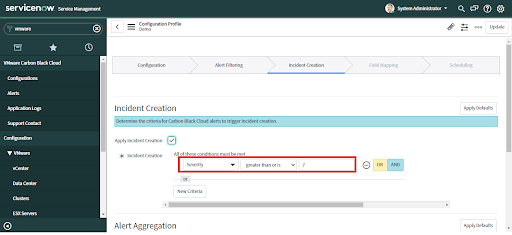
• To set custom criteria for automatic alert creation select an Incident Condition field
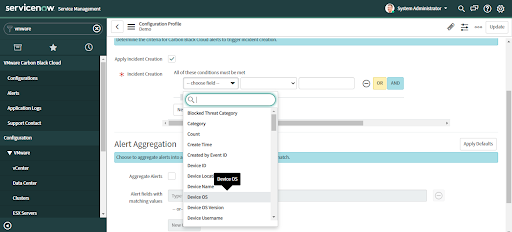
• Provide corresponding values that meet the condition.
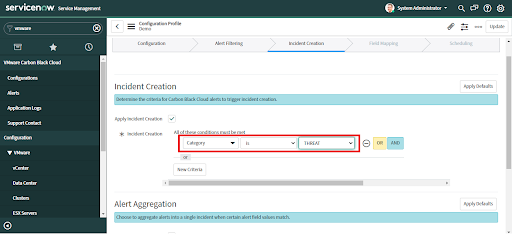
• Provide "OR" and "AND" operations to add more conditions.
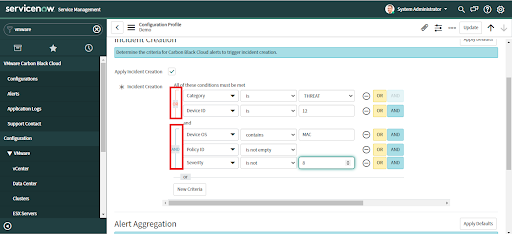
• Click on "Add Criteria" to add more conditions as needed.
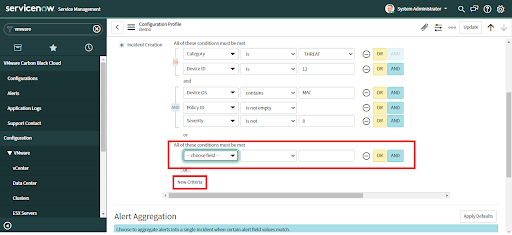
• Click the "Next" button to save changes and advance to the next tab.
Note: Only a user with the application admin role can delete the alerts. When alert(s) are manually deleted by a user and an incident is already associated to it, the user has to manage the incident manually.
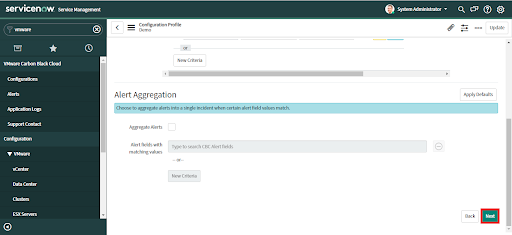
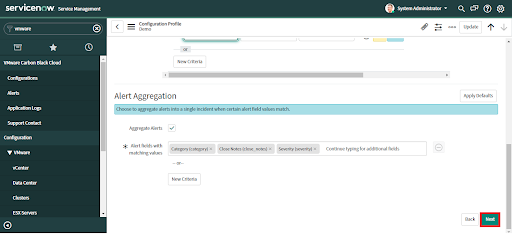
To change this configuration after the initial setup, navigate to VMware Carbon Black Cloud > Configurations and click on "Incident Creation".
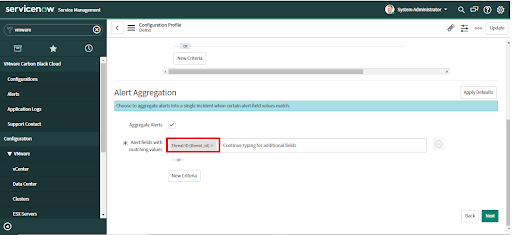
• Optional: Click on the "Apply Defaults" button to check the "Aggregate Alerts" option and populate suggested aggregation criteria.
• Review the default criteria.
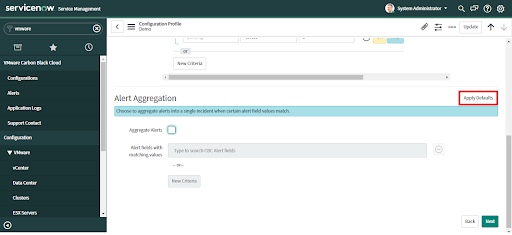
If you did not apply defaults and want to configure aggregation rules, check the "Alert Aggregation" checkbox.
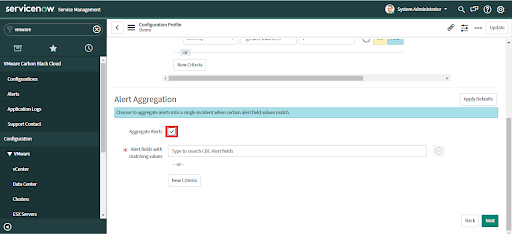
• To set custom aggregation criteria select the value from the list and press enter.
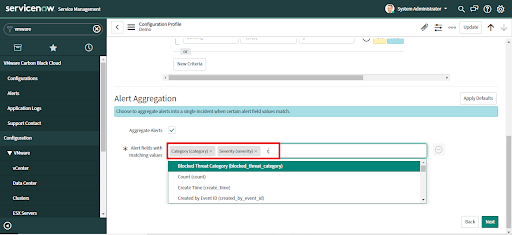
• Click on "New Criteria" to add more alert aggregation conditions
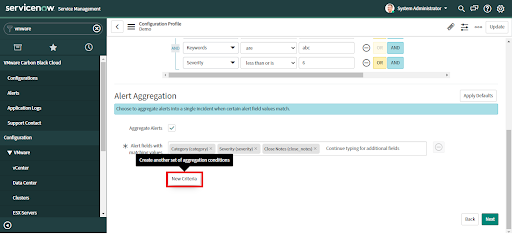
• Click the "Next" button to save changes and advance to the next tab.
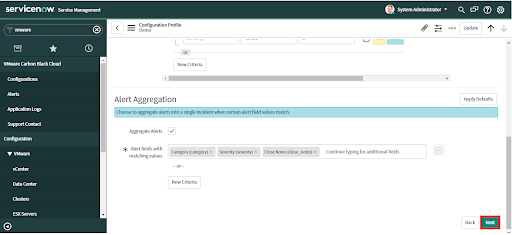
To change this configuration after the initial setup, navigate to VMware Carbon Black Cloud > Configurations and click on "Field Mapping".
• All alert fields are available for data mapping except Updated by, Effective number, Created by, Number, and Risk change.
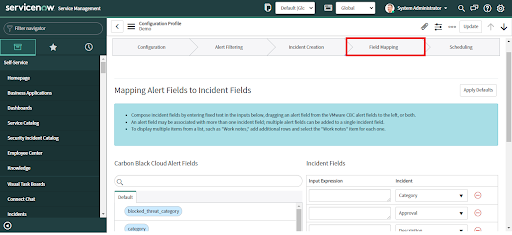
• Click the "Apply Defaults" button to get suggestions for data mapping.
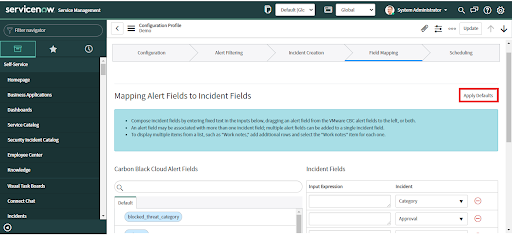
• Review the default values.
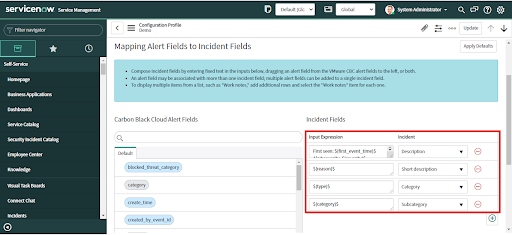
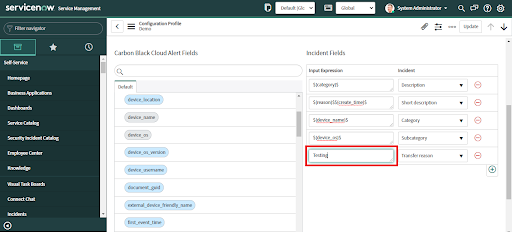
• If these are not correct for your environment, configure custom mappings
• Different Incident fields can be selected from the dropdown list as needed.
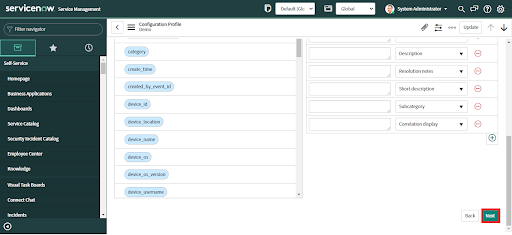
• Drag the Carbon Black Cloud alert field and drop it in the desired Incident field in the "Input Expression".
• Different Incident or Security Incident (for ITSM and SecOps Apps respectively) fields can be selected from the dropdown list as needed.
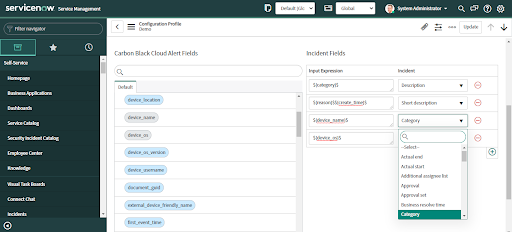
• Provide input expression values by entering a value in the text field.
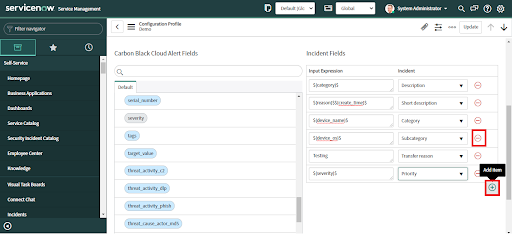
• Add or remove the Incident fields by clicking on the plus (+) or minus (-) buttons respectively.
• Click the Next button.
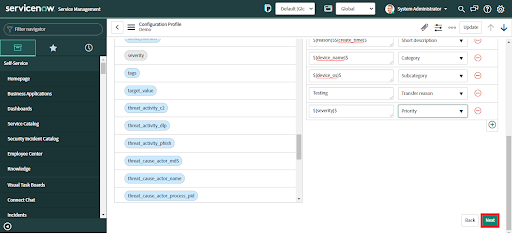
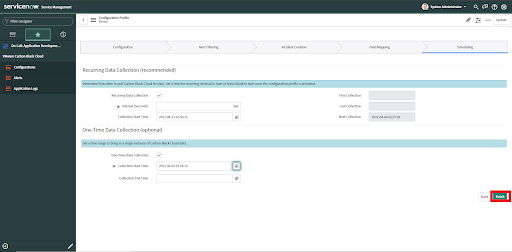
1. Recurring Data Collection - for periodic ingestion of alerts; normal running.
2. One-Time Data Collection - for example, to populate recent data on initial setup or fill in a missing period of data
To change this configuration after the initial setup, navigate to VMware Carbon Black Cloud > Configurations and click on "Scheduling".
Note: This is only supported when Alerts are ingested using the API. It is not supported for the Data Forwarder Ingestion method.
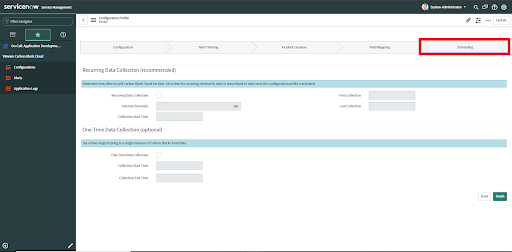
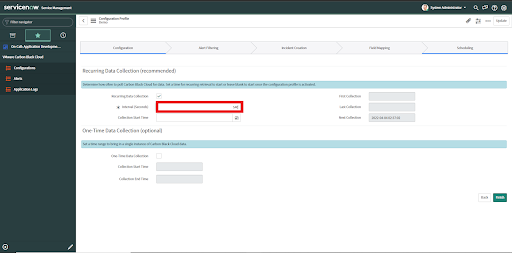
• Check the Recurring data collection checkbox.
• Enter time Interval in seconds.
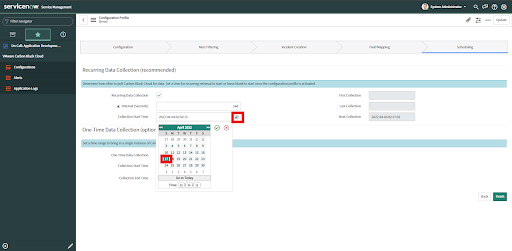
• Provide the Collection Start time as per the need from the calendar. The Collection Start date must be a future date or within 15 days prior to the current date.
Optional:
• To configure alert data ingestion for a bounded window of time in the past, check the One Time Collection Checkbox.
• Provide the Collection Start Time for the window. Only past date/times and current time-(minus)15 are acceptable as options.
• Provide the date/time for the Collection End Time of the window.
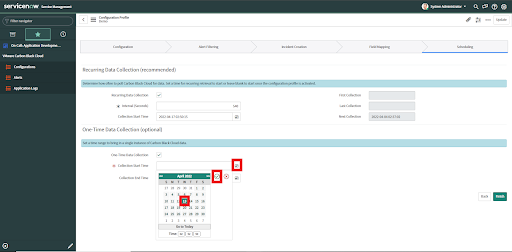
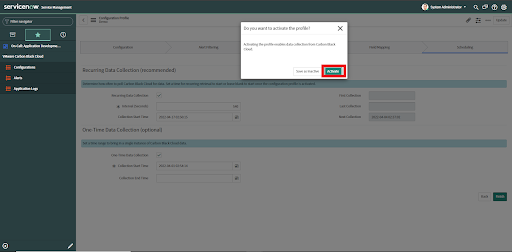
• Click the Finish button.
• After clicking Finish, a pop-up window warns that the profile is inactive and gives the option to Activate the profile or Save as an Inactive profile.
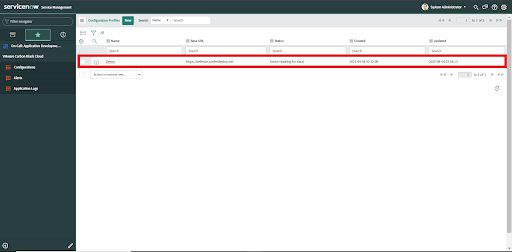
• Next you are navigated to the Configurations page where the profile created is in the list.
• Navigate to the Configurations page.
• Select the checkbox next to the profile.
• Choose the "Activate" action from the "Actions on selected rows" dropdown.
Only one Configuration Profile per Carbon Black Cloud Org Key can be active at a time. If you try to make another profile with the same Org Key, a message will appear to inform you that the profile was not activated.
Deactivate a profile
• Navigate to the Configurations page.
• Select the checkbox next to the profile.
• Choose the "Deactivate" action from the "Actions on selected rows" dropdown.
Make data easily available in related lists
-
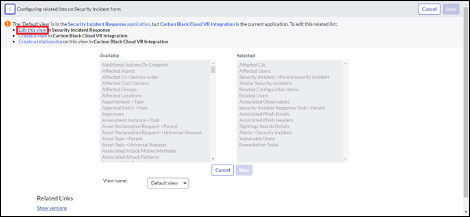
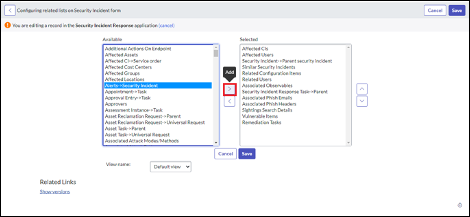
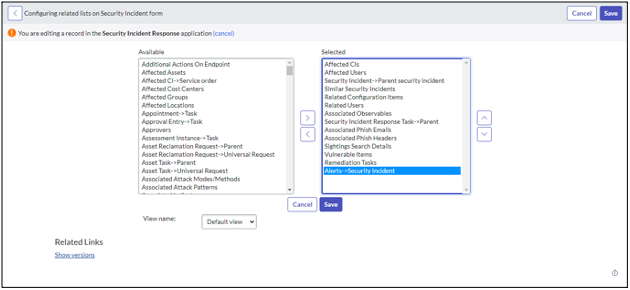
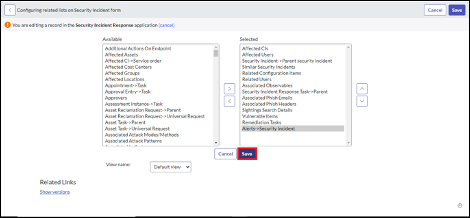
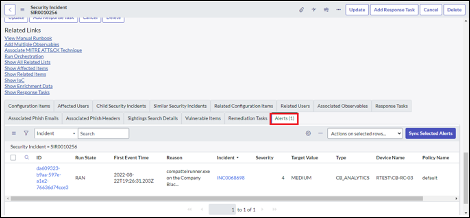
Add the Alerts tab to related list of Incidents.
To view the alerts associated with an incident in the SecOps or ITSM app, the form view must be configured in the Incidents' related list.
-
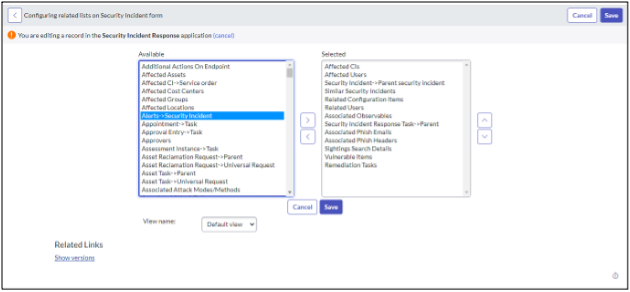
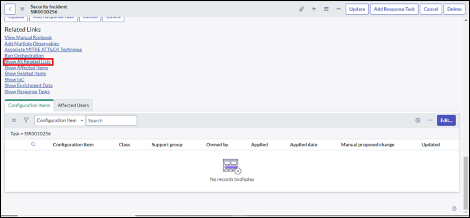
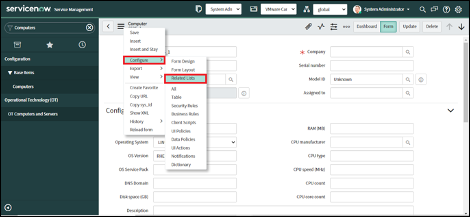
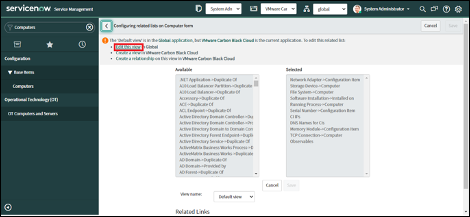
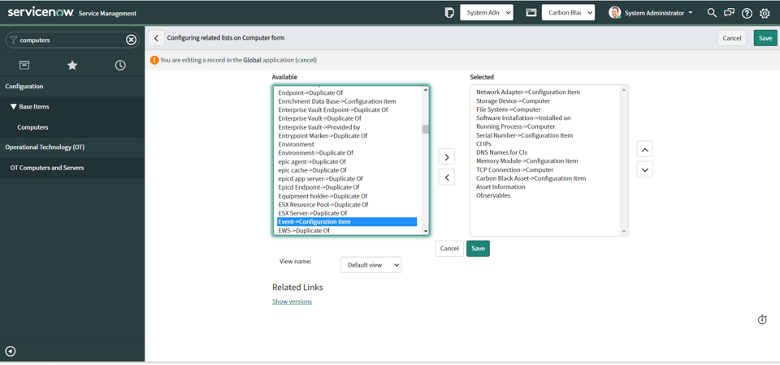
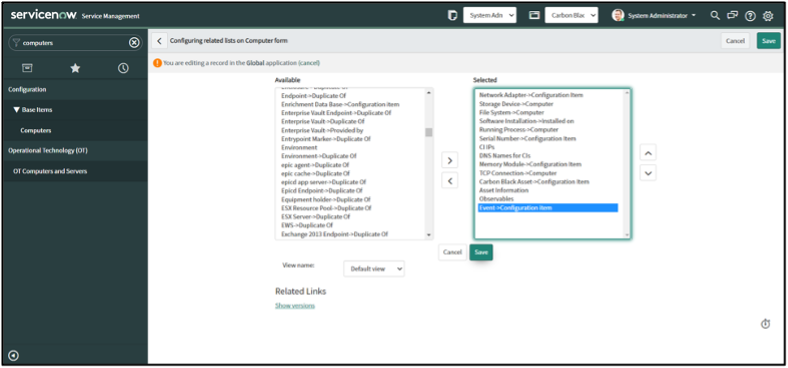
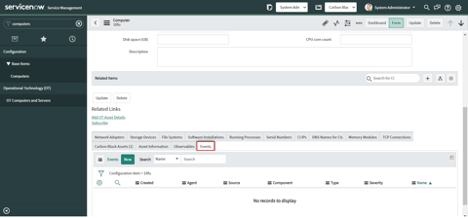
Add related lists to the “Computers” and “Virtual Machine Instances”
After configuring Asset ingest, additional SOAR actions are available on CIs in the CMDB. The following lists can be added to Computers and Virtual Machines.
- Asset Information - Get Asset Information
- Events - Get Enriched Events
- Carbon Black Running Processes - Get Running Processes at Carbon Black
- File Systems - Get Directory Information
- Process Metadata - Get Process Metadata
- Registry Keys - Get Registry Key Information on Asset
- Submit Live Query Run - Submit Live Query Run
- Alert Recommendations - Get Alert Recommendations
- Observables - Get File on Asset, Download Binary from UBS
Vulnerability Response - Delete Integration Instance
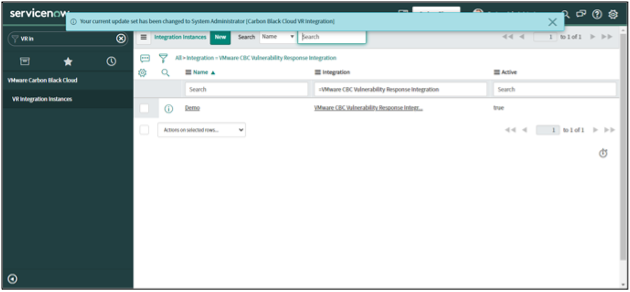
The Vulnerability Response App uses an Integration Instance. Follow these steps to delete an instance.
1. Click on Settings
2. Click on "Developer" under System Settings on the left.
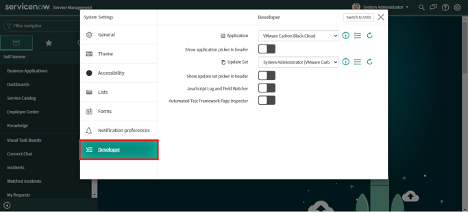
3. Enable "Show application picker in header".
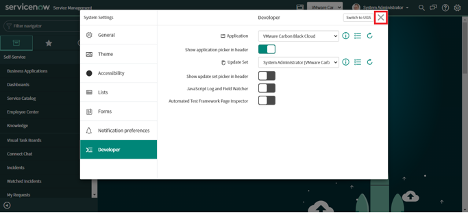
4. Click on X(Cross) to close the popup.
5. Select the "Carbon Black Cloud VR Integration" application from the dropdown.x
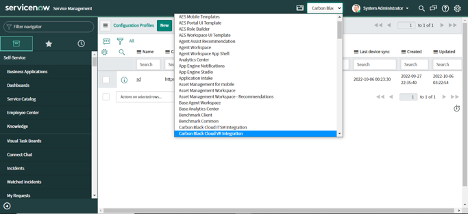
The scope of the integration instance has been set.
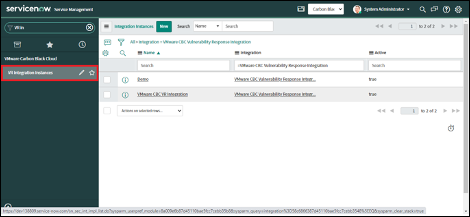
2. Select the Integration Instance that needs to be deleted.
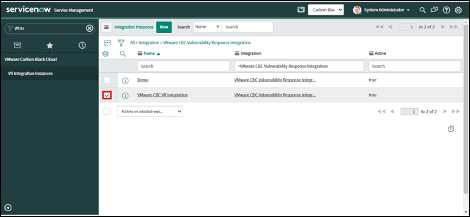
3. Click on the "Actions on selected rows" drop-down.
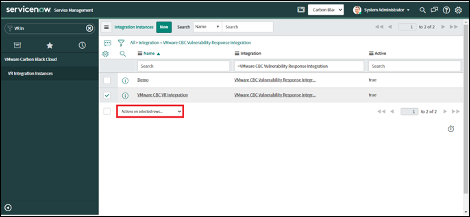
4. Click on the "Delete" option.
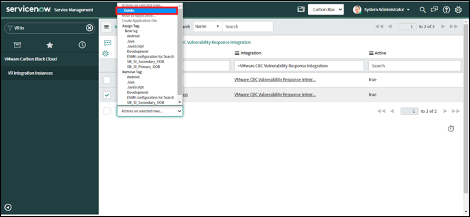
5. Click on the "Delete" button
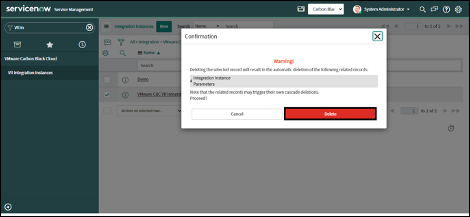
6. The Integration Instance will be deleted successfully.
Uninstall the App
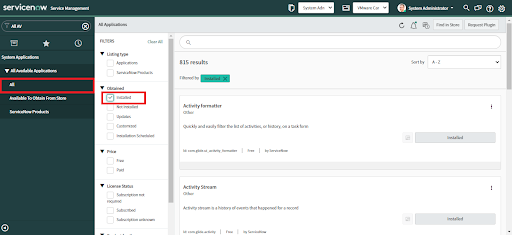
To uninstall the app, the builtin role System Administrator is required.
• Navigate to System Applications > All Available Applications > All
• Check the Installed checkbox in the Obtained dropdown.
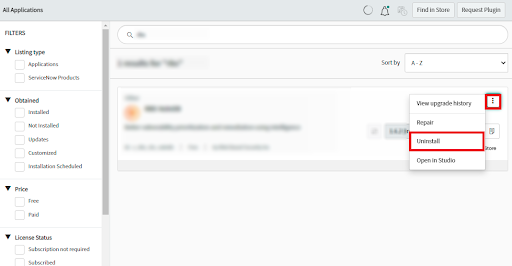
• Search for the application in the Search Bar.
• Once you locate the application, click "Uninstall" from three dots on the right side.
If the Carbon Black Cloud API Key is no longer being used, it should be deleted from Carbon Black Cloud.
Support and Resources
- Troubleshooting guide
- Use the CB Developer Network community forum to discuss issues and get answers from other API developers in the CB Developer Network
- Report bugs and product issues to Broadcom Support
- View all API and integration offerings on the Developer Network along with reference documentation, video tutorials, and how-to guides.
Last modified on February 28, 2024