Announcing Enhancements for Carbon Black Cloud App for Splunk
Posted on March 1, 2021
We’re pleased to announce enhancements to the VMware Carbon Black Cloud App for Splunk 8. This app provides an updated solution for customers to access their Carbon Black Cloud Endpoint and Workload features and data within the Splunk console. Out-of-the-box, this app provides holistic visibility into the state of your endpoints and workloads through customizable dashboards and alert feeds in Splunk.
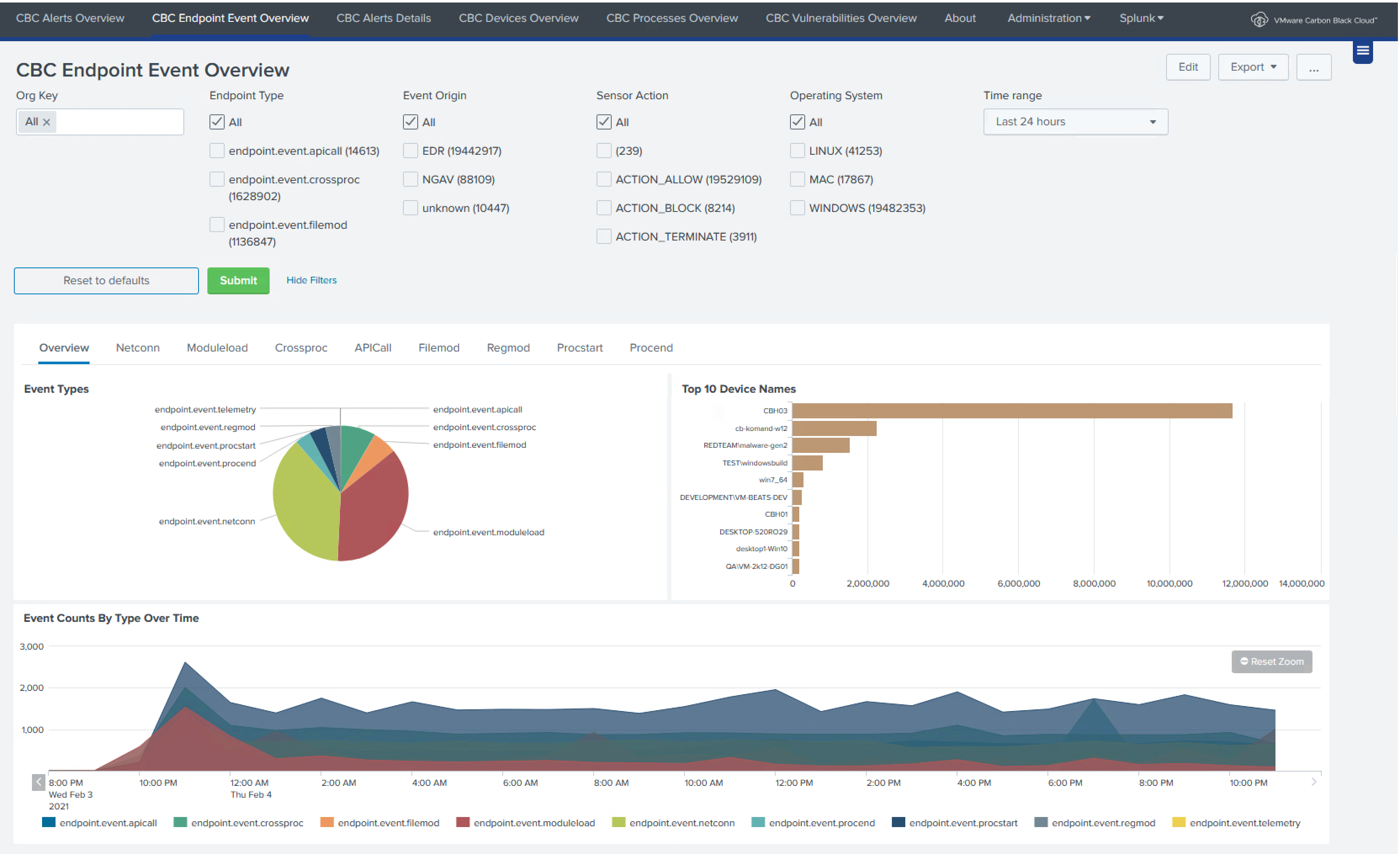
Enhancements include:
Built-in Data Inputs:
- Device Control Alerts
- Audit Logs
- Live Query Results
- Vulnerability Assessment
Common Information Model for:
- Alerts
- Endpoint/Process
- Vulnerability
- Malware
Dashboards:
- Devices
- Processes
- Vulnerabilities
Alert Actions / Adaptive Response:
- Run Live Query
- Dismiss Alert in CBC
- Update Device Policy
- Ban Hash
- Get Process Details
- Get Enriched Events for an Analytics Alert
Customers who are currently using one of the legacy Carbon Black Cloud Splunk integrations are encouraged to adopt this application in order to leverage the latest features and capabilities. Resources:
- Carbon Black Cloud Splunk SIEM App
- Download from Splunk Base
- App - VMware Carbon Black Cloud
- IA - VMware Carbon Black Cloud
- TA - VMware Carbon Black Cloud
- Read the “Deployment Guide” in the app documentation on Splunk Base to determine whether you need the IA or TA.
- In depth configuration demo videos
- Threat Hunting & Incident Response Use Cases
For questions, please reach out to the Carbon Black Developer Network.