Collective Defense & the Carbon Black Detection eXchange
Posted on June 9, 2016
It’s been an exciting few weeks for us on the Carbon Black blog. In addition to discussing the efficacy of Patterns of Attack versus Indicators of Compromise, we’ve talked about shifting the economic balance of cyber-attacks, the “story” your data is trying to tell you and, perhaps most importantly, the importance of sharing the right kind of threat intelligence to form a Collective Defense.
Today, I’m proud to reveal Carbon Black’s specific initiatives in the realm of Collective Defense in an effort to unite the cyber-security community in the battle against common adversaries.
In security, more than anything else, it’s the PEOPLE who matter most. People, not just systems and data, need to be connected to win this person-to-person war. The security industry cannot continue to perpetuate the idea that technology alone will solve our security problems. In order to change the state of security in favor of the good guys, we need to unite security experts, share best practices, the right kind of threat intelligence, and leverage open products that integrate together so people can engage with the best technology available to defeat the enemy.
Security and collaboration may never be “perfect” but we can exponentially increase the cost of an attack for malicious actors to the point where there is diminished value in attacking. For attackers, finding a “unique” vulnerability (and effectively exploiting that root cause) can take months of research, costing more than $1 million. It is no surprise, then, that attackers use and reuse the same vulnerability for years, on target after target until it is successful.
As technology providers, it is our job and responsibility to empower the community with solutions that strengthen the humans that actually provide security.
Carbon Black is doing that in a number of ways:
-
Sharing Patterns of Attack via the Carbon Black Detection eXchange – The Carbon Black Detection eXchange enables any customer or partner in the Carbon Black network to share Patterns of Attacks (POA), which identify the behavior, techniques and tactics of the attacker. Once Patterns of Attack are identified in the Detection eXchange, they can be categorized into Watchlists, to automatically detect when a POA occurs in an enterprise environment. These Watchlists continuously apply threat intelligence against new and retrospective endpoint sensor data, to immediately stop those sets of behaviors from running again, thus preventing future attacks of the same kind.
Watchlists from the community will be automatically fed into the Carbon Black Security Platform, to alert all customers when that Pattern of Attack is seen. As the community continues to share, every member organization achieves a stronger security posture. Simply put, the more attackers attack, the stronger we become as a community. Carbon Black is revolutionizing the way sharing happens. Today, almost all sharing is produced by the vendor – hub and spoke model. We are removing ourselves from the loop and allowing peer-to-peer relationships to happen.
This system makes the collective knowledge of top security experts available to every community member. This is critically valuable for organizations that previously could not afford such deep expertise. In just its first two months, more than 600 Carbon Black users have participated in the Carbon Black Detection eXchange.
Carbon Black Detection eXchange in Action
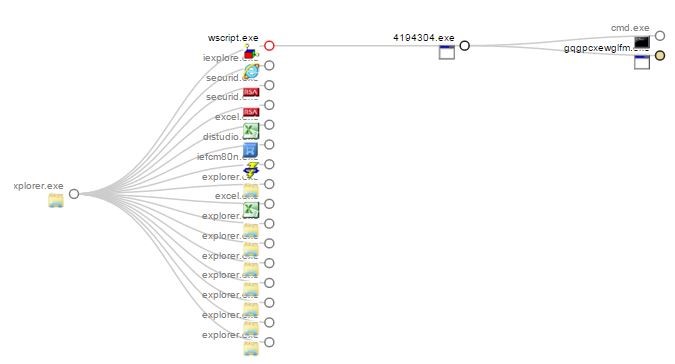
One example of the Carbon Black Community’s power in the Cb Detection eXchange is a recent discussion regarding ransomware being delivered via JavaScript. In this example, a customer shared a Carbon Black EDR query, process tree (below), and associated threat intelligence.
Other members of the Carbon Black community quickly started discussing the threat intelligence and looking in their own environments with the shared query. In this case, the initial query was looking for wscript.exe making network connections, writing new binaries to disk, and then running them. This behavior is very suspicious, but not inherently tied to ransomware delivery.
A Carbon Black employee and a few other customers collaborated with the original poster to refine the query to limit false positives. This was done by adding further criteria and context. One customer then provided the context that in his environment he’s only ever seen this activity maliciously occur when the parent process is either Microsoft Word or WinZip.
Soon after, a separate customer further clarified and refined by pointing out that the real danger for ransomware delivery is in drive-by attacks and downloads through browsers, such as Google Chrome and Microsoft Internet Explorer, and email clients such as Microsoft Outlook (shown in the process tree below.)
The collaborative effort of the Carbon Black community turned a piece of threat intelligence into a much more fine-tuned piece of actionable threat intelligence with significantly less false positives. The query started as a single suspicious process and crystalized into a descriptive Pattern of Attack (seen above in the process tree). The Pattern of Attack shown is: Outlook opens a Word attachment, which runs wscript.exe, which runs a script, which calls out to a server, downloads a malicious exe., and runs it.
The end result of this collaboration is now available in the EDR product through the Carbon Black Threat Intel Community feed.
-
Openly Published APIs – As a further commitment to empowering the security community via Collective Defense, Carbon Black has openly published its APIs and open-sourced all of its third-party integrations. The number of integrations available continues to grow and will be a key component to our philosophy. We want to spearhead the effort in seeing the entire industry become stronger in defending against attacks. Our open platform is a major part of that.
-
Carbon Black Developer Network – The Carbon Black Developer Network embraces two fundamental tenets. First, our products are actually platforms, where the power within them can be tailored and optimized through integrations and automation for an organization’s specific needs.
Second, the open-source movement has shown itself to be fruitful. Reusing code, learning from each other, and crowdsourcing the building and validation of use-cases simply works, and that’s why we’ve made a push to create APIs, documentation, and encourage sharing among our user community.
In this network, created by the Carbon Black Developer Relations team, security defenders on the front lines can make sure they get the value that they need, versus being locked into a rigid product that won’t mold itself into the larger security ecosystem.
We are very passionate about “uniting.” It was a founding principle when we decided to build Carbon Black and I am confident it will be a rallying cry for the entire industry when the power of Collective Defense.