Announcing Threat Tracer a New Investigation Tool for Carbon Black Cloud
Posted on June 30, 2025
What is Threat Tracer?
Threat Tracer allows visual analysis and exploration of threat data gathered by Carbon Black Cloud Enterprise EDR .
Investigation results are captured in a graph. The fundamental components of a graph are entities which represent the various elements that make up an event — such as processes, users, assets, or domains. These entities are linked by relationships, which describe how one entity was connected to or interacted with another in the historical data collected by the sensor. Examples of relationships include child process, process user, and executables written.
Unlike static process trees, Threat Tracer gives you a dynamic, user-driven, visual map of relationships to quickly uncover root cause, lateral movement, and impact. In enabling you to connect disparate data points across your whole organization in a single view, Threat Tracer can bring a bird’s eye view to triage, investigation, and response activities.
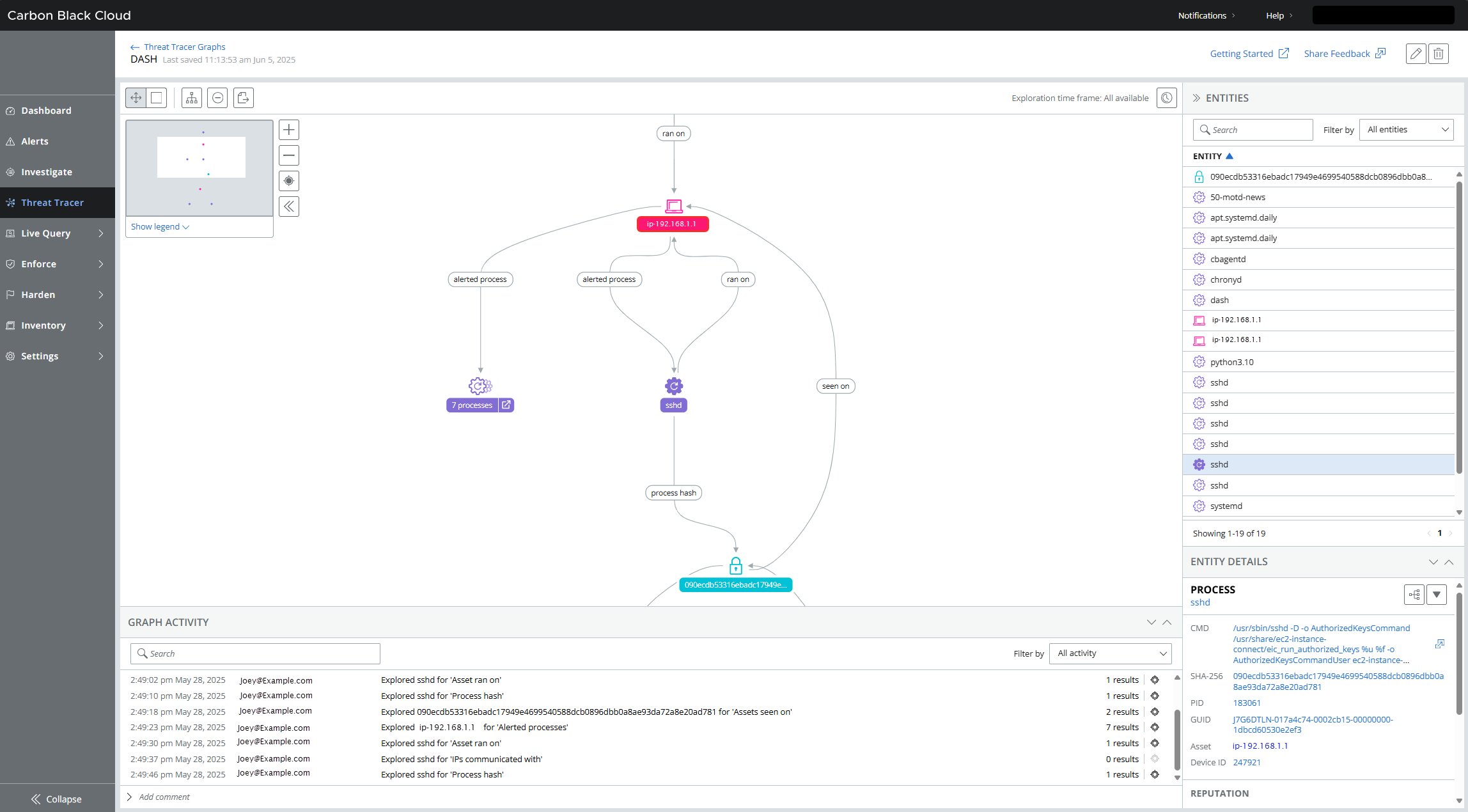
Why use Threat Tracer?
Threat Tracer allows Incident Responders (IR), Threat Hunters, and SOC Analysts to easily visualize, analyze, and contextualize complex threat and security data. With Threat Tracer, you can map out relationships between various security datapoints, track incidents, and gain a clearer understanding of potential threats across your environment.
Threat Tracer eliminates the need for manual pivoting between views or writing complex queries. Analysts can visually trace connections between suspicious activities, discover root cause faster, and communicate findings more clearly with shareable graphs.
Example Use Case: An analyst is investigating a suspicious alert and opens a Threat Tracer graph for the parent process. Using the visual map, they identify a child process that made unusual external connections and downloaded a payload — confirming a phishing attack chain in under 10 minutes.
Learn more: User Guide