Back to Blogs
Reminders of Recommended Practices for Securing API Access
Reminders of Recommended Practices for Securing API Access
Posted on January 29, 2024
Overview
Credential theft is a common technique used by threat actors to gain access and persistence. User credentials are often the main target for these activities. However in recent years, the security industry has seen an increase in theft of cloud access credentials such as AWS access keys. Access via APIs is a powerful way to integrate Carbon Black Cloud into your ecosystem. That access should be managed and reviewed periodically, as you would user access. Here are some tips to improve the security posture around Carbon Black Cloud API Keys.
Tips
- When you create a new API key, store the API Secret securely as you would a password.
- After the initial creation, the API Secret can be regenerated, but not recovered.
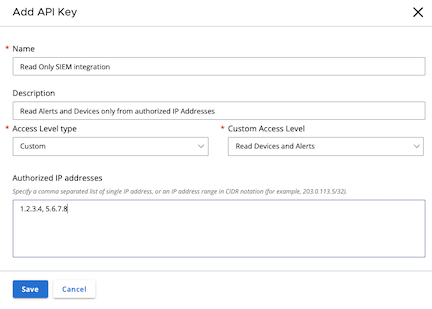
- Limit access to the minimum required by the API Key by creating an Access Level with only the permissions needed
and assigning that Access Level to an API Key with an Access Level of type Custom.
- Read more in the Carbon Black Cloud User Guide.
- Read more in the Carbon Black Cloud User Guide.
- Restrict access to specific IP Addresses.
- Monitor Access via API Keys as you would user access
- Review the audit log:
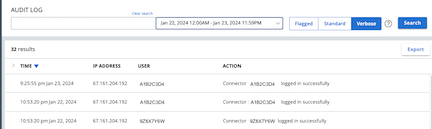
- Review the last time the API key was used
- Go to Settings > API Access and check the
Session Renewal Time. This will show the last time the API Key refreshed its session.
- Go to Settings > API Access and check the
- Look for anomalies
- If an API Key is being used to poll every 5 minutes, expect to see an Audit Log each time the
authentication session is renewed (approximately 15 minute intervals). This can make it difficult to see anomalies in the usage.
Use a query in the Audit Log Search bar to remove expected Audit records. This example removes any entry for session renewal & alerts API usage. What’s left are actions you might not expect the key to be doing, and actions being done to that key.
A1B2C4D4 -"logged in successfully" -"Getting alert" -"Getting threat"- That query translates to “Find all the audit log records that include
A1B2C4D4and do not include any oflogged in successfully,Getting alertorGetting threat”.
- If an API Key is being used to poll every 5 minutes, expect to see an Audit Log each time the
authentication session is renewed (approximately 15 minute intervals). This can make it difficult to see anomalies in the usage.
Use a query in the Audit Log Search bar to remove expected Audit records. This example removes any entry for session renewal & alerts API usage. What’s left are actions you might not expect the key to be doing, and actions being done to that key.
- Review the audit log:
- Remove access when it is no longer needed
- Regenerate the API key and store it securely - this will prevent access using the previous secret while allowing full visibility into the access the API Key has if needed. If the API Key is needed, provide the new API Secret.
- Delete the API key when you’re sure it’s not needed.
- Consider rotating keys on a regular basis. This brings the benefit that if the key has been compromised and the threat actor is holding on to it, you’ve eliminated their means to access.
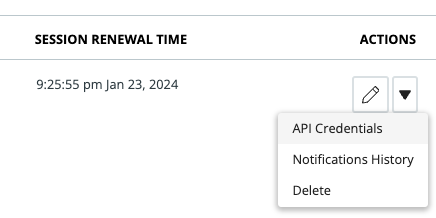
- To regenerate an API Secret Key, go to Settings > API Access and find the API Key that you want to create a new secret for.
- Click the Actions menu and select
API Credentials. - Click
Generate new API Secret Keyand confirm. - Record the new API Secret Key securely and update integrations as needed.
- The previous API Secret Key becomes invalid immediately.
- See the Carbon Black Cloud User Guide for details
Requirements
- Carbon Black Cloud
- The User requires a role that has:
- Manage Access Levels
- Manage API Keys
- View API Keys
More Information
- Authentication Guide on the Developer Network
- Setting up API Access in the User Guide
- Integrations and Toolkits to integrate with Carbon Black Cloud
Have questions or feedback?
- Use the Developer Community Forum to discuss issues and get answers from other API developers in the Carbon Black Community
- Report bugs and change requests to Carbon Black Support
- Subscribe to the Developer Network Newsletter