New Release: Binary Toolkit for the Carbon Black Cloud
Posted on June 26, 2020
We are happy to announce the 1.0 release of the Carbon Black Cloud Binary Toolkit.
What is it
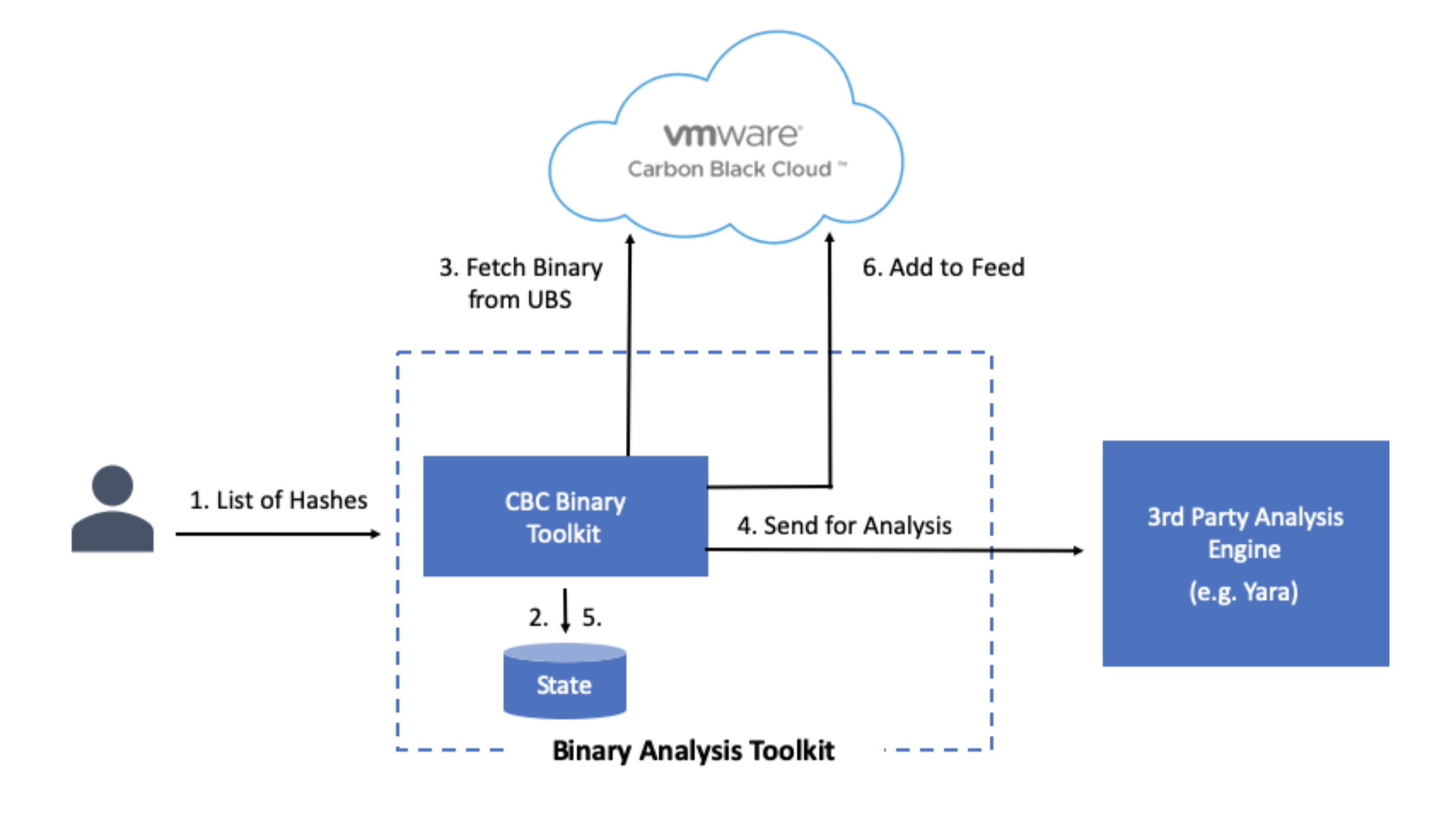
The Binary Toolkit lets you integrate between Carbon Black Cloud Enterprise EDR and a binary analysis engine, like YARA. When the toolkit receives hashes of binaries encountered by your organization, it sets off a process where it fetches metadata about the binaries from the Unified Binary Store (UBS) and then sends the binaries through the analysis engine. The results from the engine and the metadata are consolidated and sent back to the Carbon Black Cloud where you can subscribe and monitor your environment in Watchlists.
Who is it for
This is for customers and partners using Carbon Black Cloud Enterprise EDR who send binaries to the UBS and have a suite of YARA rules or another analysis engine to use with the binaries.
What changed?
There were no major changes from the Alpha release in May. Changes that did occur include:
-
Minor Bug Fixes
-
Completion of end to end testing on a variety of operating systems including CentOS, Ubuntu, OpenSUSE and Windows Server 2019
-
Scale testing — see information about scale and performance here
Get Started
Out of the box, it can be installed using pip install and then configured to:
- Begin processing with an input list of hashes
- Retrieve metadata about those hashes from the UBS
- Forward the URL for the binary to an analysis engine
- Receive the results of the analysis
- Add the results to a feed in Carbon Black Cloud as a report
Watchlists can also subscribe to Feeds for continued monitoring.
The state is stored in memory and is managed by SQLite persistence store by default. This enables continuation of processing after failures and deduplication of hashes for analysis across multiple executions.
- Installation from pip install is available here
- GitHub repository can be found here
- User Guide can be found here
- Developer Guide can be found here
Using the Binary Toolkit with YARA Integrations
The YARA Rules engine is an example of an analysis engine that can be used with the Binary Toolkit. The YARA-python library runs in-process and is ready for your rules to be added. To add a different engine or move to an out-of-process engine, see the Developer Guide.
- Use this when an unknown or known-malicious binary attempts to execute in an environment (and is detected by Carbon Black).
- Send the SHA-256 hash to the Binary Toolkit in order to analyze the unknown binary for threats and vulnerabilities.
- The Binary Toolkit will fetch the metadata and an AWS S3 download url for the unknown binary from the Unified Binary Story within the Carbon Black Cloud
- Then the YARA engine will analyze the binary against the compiled YARA Rules to identify any matching patterns within the unknown binary.
- The YARA engine will return an IOC if any of the rules matched against the unknown binary which will be fed back into the Carbon Black Cloud to act like a signature, identifying and alerting on this malware if it is detected again within the environment.
How can the toolkit be extended?
The toolkit also provides a base that allows you to extend, which helps reduce the time required to create integrations for analyzing Carbon Black Cloud binaries. See the Developer Guide for information on how to use a different analysis engine or change the datastore used for state management.